With over 2 billion text and multimedia messages sent in the United States annually, the use of MMS is one of the most prolific messaging systems. Despite this, few people stop to consider the critical question: Is MMS safe?
MMS messages are not safe, secure, or private. The Multimedia Messaging Service does not protect text, audio, photos, or videos sent from a mobile phone. Your mobile service provider has access to the transmitted content. There are alternatives to MMS and SMS messaging that are end-to-end encrypted.
Let's take a look at why you should stop using MMS messages now. I've also included the 5 messaging apps you should use instead of your junky insecure texting app.

Is MMS secure?
Any purely text-based message is usually sent as a Short Messaging Service (SMS) message. An MMS message is essentially any text message that includes media: pictures, audio, videos, emoji, and links.
As you text people, your messaging app moves seamlessly between SMS and MMS. Depending on the message type, you could be sending hundreds of completely unprotected MMS messages a day.
While SMS messages were first developed in 1984 and first used in 1992, MMS is slightly younger, coming to market in 2004.
That's right:
MMS is ancient in technology terms. And because it's such old, it was developed long before privacy was a concern.
Mobile service providers keep logs showing who, when, and where you message when you use MMS.
They also have full access to what you sent. Your private text, photos, and other media are available to them for years since the content is not encrypted and stored on their servers.
Today, we do a lot of work on our phones. Some of us are doing actual work on our phones during the business day - dealing with client data, accounts, and other critical information. Others among us are transmitting personal information that can be pretty private.
So, if SMS and MMS aren't safe, what can we do to protect ourselves? Is there such a thing as secure MMS?
Is MMS end-to-end encrypted?
MMS is not end-to-end encrypted. The Multimedia Messaging Service was developed when data transmission was costly, leading to the exclusion of message security. Mobile phones were not powerful enough to handle encryption and decryption. Today, there are more secure and private ways to send messages.
The decision to exclude message encryption was a dangerous move and opened several security issues.
In addition to allowing access to breaching hackers, snooping governments, and unscrupulous cellular carriers, text users, especially Americans, have never altered their habits or upgraded their technology to avoid being spied upon or a cybersecurity victim.
This means that even though they may know about end-to-end encryption apps, many still don't bother switching to them. They continue to send unencrypted text messages via their carrier networks out of convenience or indifference to their privacy or the privacy of their recipients.
What if I don't care about my privacy? MMS is old, but it's battle-tested and reliable, right?

Should I use MMS?
It is recommended to stop using MMS messages. The outdated technology behind multimedia messaging cannot protect message privacy. The availability of low-cost cellular data and smartphones means users can easily switch to one of many secure and encrypted messaging apps to phase out MMS use.
While billions of these outdated MMS messages are sent annually, most people outside the US do not use MMS for sensitive information anymore.
Americans are the only ones who still regularly use MMS and SMS for all messages regardless of the sensitivity of the content. US users have been uniquely hesitant to transition - and equally unconcerned about privacy.
The rest of the world transitioned to messenger apps long ago due to the expense of using SMS and MMS.
Of course, the rest of the world isn't just using messenger apps because of privacy concerns. Messenger apps also have a lot of features that MMS doesn't have. Most messenger apps can:
link messages to profiles
send very long text content
display full-resolution photos and video
exchange any type of data file directly
Because MMS is such an old technology, it often has to compress content, break up text streams, or reject incompatible or large files -- on top of being inherently insecure.
In fact, even using iMessage is dangerous. Those not using Apple's messenger receive "Liked" text messages and here's why that's bad.
So, why are most people still using MMS?
Many people don't realize MMS has security issues. Additionally, since SMS and MMS are built into any mobile phone or smartphone purchased, it's easy to use the outdated technology by default, never thinking about the potential consequences.
Some attempts have been made to transition from MMS to the newer RCS (Rich Communication Services) protocol...which may not be much better.
What is RCS Messaging & Is It Safe?
RCS messaging was developed in 2007, making it nearly as old as MMS. It was intended to replace SMS and MMS, rolling both services into a single protocol.
Many major carriers use RCS messaging, and it's frequently used by Android phones to mimic Apple's iMessage functionality. But RCS messaging wasn't rolled out to all carriers.
Apple does not support RCS, which means Android and Apple users do not have a unified system to securely exchange messages. (Android users can't receive an iMessage, and an Apple can't receive RCS message).
On top of the patchy RCS adoption, the protocol does not solve the primary privacy problem of SMS and MMS; there's no end-to-end encryption.
For that matter, while Apple-designed iMessage with end-to-end encryption in 2011, this benefit is only leveraged within the company's ecosystem of products.
Note:
Apple states that it cannot access iMessage content. However, the company started implementing on-device scanning of photos to combat illegal child abuse.
The core problem with iMessage is that it only delivers security to iPhone and iPad users. If you have a text message chain or group chat that contains a single Android user, you will be immediately dropped into MMS mode.
Like iMessage, RCS provides users surface-level functionality to make it more like a modern messaging app, making it easier to send longer messages and bigger files. But RCS is not secure, and therefore it isn't a good solution for private messages.
The best solution is something most of the world is already using: an encrypted messaging app.

Which is the safest messaging app?
The safest messaging apps are:
Signal
Telegram
Element
Briar
Session
After testing each messenger, the order above is a good balance between ease of transition for the average user and message privacy/security.
Here's why I like each of these messengers.
| Messenger | Biggest Advantage | Worst Disadvantage |
| Signal | Easy to switch to | Requires phone number to sign up |
| Telegram | Excellent user experience | Custom encryption protocol |
| Element | Decentralized servers | Not plug & play; some technical knowledge required |
| Briar | Multiple ways to transmit messages | User experience needs work |
| Session | Blockchain secured | Low number of active users (for now) |
Average MMS Users Should Switch To...
For many users, the most accessible secure messaging app to use is Signal messenger.
Signal messenger was developed in 2015 and incorporates many advanced features that users expect to find in their messaging systems today. Of course, the primary reason to switch to Signal is to take advantage of the end-to-end encrypted message functionality between you and other Signal users.
Signal is the easiest way to stop sending insecure MMS messages for the average user.
The Signal messenger can be used to handle both insecure SMS and MMS messages. I recommend against using the same app for both.
Separating secure and insecure communication between the different apps will help you avoid accidentally leaking your sensitive information to third parties. For example, if you're texting someone not on Signal yet, those texts will stay in your old texting app.
Some features of Signal include:
Being able to set the color, theme, and background picture of chats. You can personalize your communications through Signal, creating a more friendly and custom atmosphere - and making it easier to see at-a-glance who you're messaging.
Being able to set messages to "disappear." Like Snapchat, messages in Signal can be set to destroy themselves after a certain amount of time.
Being able to archive and unarchive messages. If you're no longer in a message chain, you can archive it to declutter your chat list. You don't have to just delete the messages and lose them forever.
Sending payments. Signal also provides the ability to send in-app payments. Send a payment for a movie ticket, buy dinner together, or otherwise reimburse people you know.
Using either WiFi or cellular data. You have the choice to go through WiFi or cellular data, which can save you money depending on whether you have a restricted data plan.
Snapchat Break:
In the following Surveillance Report on the Techlore YouTube channel, Nathan uncovers a story about how Snapchat actually handles expired direct messages on Android devices. While this isn't a security vulnerability, he explains what you should do to ensure the expired messages are deleted. I've fast-forwarded the video below to that story.
Tech-Savvy Users Should Switch To...
For the more tech-savvy reader, take a look at The Briar Project.
Briar doesn't use personally identifiable information like a phone number or email address to sign up for an account. Typically messaging systems use a phone number to prevent spam or robot account creation since there are a limited number of phone numbers in the world.
Briar is used by those who need to keep their communications secure and anonymous. It leverages the Tor network and peer-to-peer connections to route messages.
Unfortunately, it's not available for iOS devices. Android users can install the app from the Google Play and F-Droid app stores or directly from the project's download page.
Some features of Briar include:
Surveillance and censorship protection: Briar is instrumental in areas where the government may engage in surveillance or censorship, such as areas where the political situation may be inherently unstable.
No meta-data spying: Briar protects users from meta-data spying by stripping out any sensitive information and keeping the user's data highly local, rather than maintaining a copy synchronized to the cloud.
Server-less architecture: Data isn't stored on servers but instead transmitted peer-to-peer end-to-end encrypted. This eliminates the chances of a single server becoming a vulnerability.
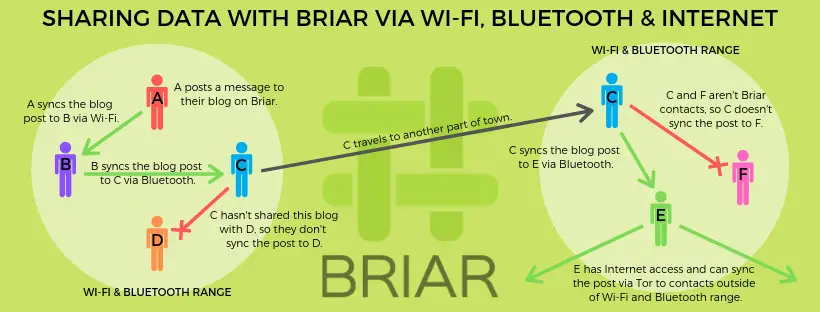
Operable during internet and power blackouts: Briar uses a smart grid or peer-to-peer architecture. It can be used even if the cellular network and internet services go down. Passing messages can be accomplished between mobile devices via Bluetooth connections or over an internet-disconnected WiFi network.
🛑 PLEEEASE: Do not use WhatsApp.
You'll notice I did not mention the world's most popular messaging app here. This is for a good reason.
While WhatsApp advertises end-to-end encryption, this only secures your content. The metadata about your conversations is not secure, and the company regularly hands over user metadata to third parties and governments. Facebook also mines the metadata connections between users.
Using WhatsApp is (I guess) slightly better than MMS and SMS messages but not by much.