We receive about 15 spam text messages per month. While some Short Message Service (SMS) messages are frequently annoying marketing texts, others are clearly hacking or phishing attempts. I've received my share of texts that are harassing which made me wonder: How do you figure out who's sending these messages? Can a text be traced?
Text messages can be traced. This 1990s technology was designed before security and privacy were a consideration. Mobile service companies must keep logs of text data for law enforcement, including a general location. The average person has a few ways to track the origin of texts.
If you've received spam text or multimedia messaging service (MMS) messages or wondering how hackers send them, read on. Let's explore some ways an average user can find the source of their unwanted texts.

How To Track A Text's Origin For The Average User
Most users can start to track a text message's origin by noting the area code of the phone number that sent the SMS text.
The North American Numbering Plan (NANP) organizes phone numbers for the US, its territories, Canada, Bermuda, and seventeen Caribbean island nations. The first three digits identify an area that can hint as to where the text message originated.
Unfortunately, several factors make tracking a text's origin less accurate by area code:
Free Mobile Roaming: subscribers can keep their cell phone number regardless of where they use their phone within the country.
Internet Telephony: internet-connected phone calls and texting means that a number can shift owners quickly, and phone number spoofing is inexpensive.
Email-To-SMS Gateways: many mobile companies provide email addresses to each serviced phone number.
It is risky, but if you have a burner phone number or other means to make an anonymous outbound call that won't expose your real phone number, you can consider calling the number that texted. Frequently, this results in reaching an out-of-service number but may yield the identity of who texted you.
A) Using Online Services For Text Message Tracking
If you have the sender's phone number, you can start your investigation using a reverse phone number lookup service like BeenVerified or Spokeo.
Both of these services allow you to search through public records from multiple sources, including landline telephone directories, social media profiles, credit reports, etc. The results may give you clues about the person, business, or service that sent the text.
Tip:
Consider doxing yourself. Searching for your information using your real number or address within the above services to see what's available about you online. It's eye-opening to know just how much data is available.
B) Using Your Mobile Service Company For Text Message Tracking
With the results from your public records search in hand, contact your mobile service provider for help. Explain your situation and that you've gathered some initial identifying information.
The cellular company will have some ability to provide you with specific information about the subscriber or inbound text sender. Still, it's worth asking for more details and guidance. They may also be able to block the number from calling or texting you in the future.
C) Using The Law Enforcement For Text Message Tracking
If you don't get any helpful answers, contact your local police or law enforcement agency with jurisdiction over the area where the original text came from.
Federal communication regulations require all telephony providers to maintain call logs and text records on subscribers.
This can be a good and a bad thing.

Can Law Enforcement Trace Text Message Sources
Law enforcement with a court order can compel a cellular company to provide the content and metadata of a text message. Mobile service providers typically retain SMS/MMS content for several days. The meta-information about a text is available for years, which can help trace a text.
The metadata about a text can lead law enforcement to identify the source or sender of the message.
Ideally:
A judge carefully reviews the evidence surrounding the request to obtain call and text records and then issues a search warrant.
But police and various agencies have found ways to use easily-obtained administrative subpoenas to order telecommunication companies to access specific detailed logs.
Traditional cellular service providers along with virtual number/voice over IP (VoIP) companies must comply with legal orders to obtain subscriber data.
For example, a TextFree number can be traced by request through their legal compliance department. This is similar to TextMe, Hushed, or any similar virtual calling and texting app.
Even if a subpoena is not obtained from judicial sources, police can track your phone messages with several technological solutions. A couple of these technologies exploit the fundamentals of how messages are transmitted and stored on your cell phones.
If police know the general location of text senders, they can deploy devices known as stingrays. These cell-site simulators or IMSI catchers act as man-in-the-middle attacks for Mobile Cellular devices capturing both call and text Data then forwarding it to destination service providers.
Law enforcement may also be able to retrieve text messages via the Cellebrite Universal Forensic Extraction Device (UFED). This machine can recover text messages from dumbphones and smartphones, including deleted texts and multimedia messages with physical access to a phone.
Using a secure messenger that does not use the old SMS or MMS protocols makes tracking data to transmit text and multimedia messages more difficult.
Later, I've detailed how attackers can send texts that make it difficult for anyone to track the source.
FAQs
1. Should I Open A Text Message From An Unknown Number?
Generally, it is not good to open text messages from unknown numbers. Viewing an SMS and MMS message is unlikely to cause a phone to be hacked. It is essential to not tap links, open media, or download attachments from unknown senders. Concerned users should delete texts from the messages list.
True Story: My financial advisor texted me from his mobile number (previously unknown to me) and included financial and personal information. I asked him to call in the future, explaining that SMS is insecure and logged. Sheepishly on the voice call, he assured me that he had deleted the texts. This illustrated a general misunderstanding about how messaging works. I explained that old-school text messages are not linked phone to phone. Being a smart guy, he quickly understood that he had only deleted his copy of the message. I wonder how many other clients he had texted. 😬
In this case, I used the short preview of the text, deciding to open the message, which I usually would have deleted straight away.
What about scammers or people that know your phone number? Can they hack you?

2. Can Someone Hack You With My Phone Number? 3 Potential Methods
It is typically not possible to directly hack a smartphone with only a phone number. Most exploits require some action by the phone's user to execute. So-called interaction-less bugs in messenger apps and mobile operating systems are rare and quickly patched. Select apps and services carefully.
A) Apps & Communication Services
Many communication apps may be poorly written and leak data or intentionally used to exploit access to a user's phone number, data, and device. Be selective and cautious whenever installing new smartphone apps or creating an account for that trendy, new free service.
B) Messenger & OS Bugs
Even with caution, attackers have discovered and exploited both iPhone iOS devices and Android smartphones allowing access without interaction. These are highly sophisticated attacks in a rare but underscore the importance of keeping your mobile device updated.
C) Social Engineering
Social engineering is a way of manipulating a target to perform a desired action on behalf of an attacker.
A hack can be launched with only a phone number by tricking a victim into tapping a link or downloading an app.
Today's smartphone users have low attention spans and are chronically overworked leading. These conditions lead to an inclination to act reflexively without analyzing a text instruction received.
To avoid SMS-based phishing attacks, also called smishing, I recommend simply deleting messages from numbers, not in your contacts list or unknown email addresses.
3. How Do You Stop Receiving Spam Texts?
The best ways to stop receiving spam texts:
Never click links in texts
Never reply to messages
Mark text messages as spam
Block messages from unknown numbers
Turn on caller ID block except for friends or a family member
Add your number to the National Do Not Call Registry
Forward spam texts to 7726 (SPAM) in the United States
Do not install low quality iPhone and Android apps
Better yet, just stop using SMS & MMS messages.
Encourage the important people in your life to switch to a secure messaging app. Then ignore or even turn off notifications on your standard messages app.
| Here's a list of encrypted messenger apps to check out. |
So, where do hackers get your number, and how do they send texts?
4. What Are The Common Sources Of Unknown Texts?
Over the decades, SMS and MMS have been patchworked into modern systems as users have demanded features and refused to switch away.
The age integration of the 90s technology itself can be blamed for the difficulty of tracking and the ease of malicious actors in anonymously sending messages.
A) Text via A Burner Phone Number
The movies portray a rogue hacker sending a text to his victim via a burner phone he picked up at a convenience store. After sending the message, he pulls his jacket's hood over his head, takes apart the device in a few seconds. The hacker casually tosses the pieces in a nearby trashcan, walking away down a dark alley.
While this is a feasible way to send texts so a recipient can't trace the sender, for large-scale text campaigns, it's inefficient to send messages from a single burner number.
B) Text via Online Services
With the rise of SMS-based marketing, several companies similar to SlickText offer inexpensive packages to send SMS and MMS messages. This type of service requires that permission be granted by a list of uploaded recipients.
It's not difficult to imagine that an attacker may launch a mass text campaign knowing that it may be their only campaign from a similar texting service.
C) Text via Email
Shockingly, your mobile phone company provides a free way to send texts to subscribers that's mostly untraceable.
Cellular companies offer what's called an email-to-text gateway open and free of charge.
Each subscriber's phone number has an email address automatically assigned. Sadly, this is a vulnerable access point for attackers to send unsolicited text messages to users.
I tested my provider's email-text gateway service and received simple texts, links (most messengers will make them clickable), images (which showed up automatically), audio, and video files. Fortunately, the document and other more dangerous attachments I sent did not land in my phone's text chat.
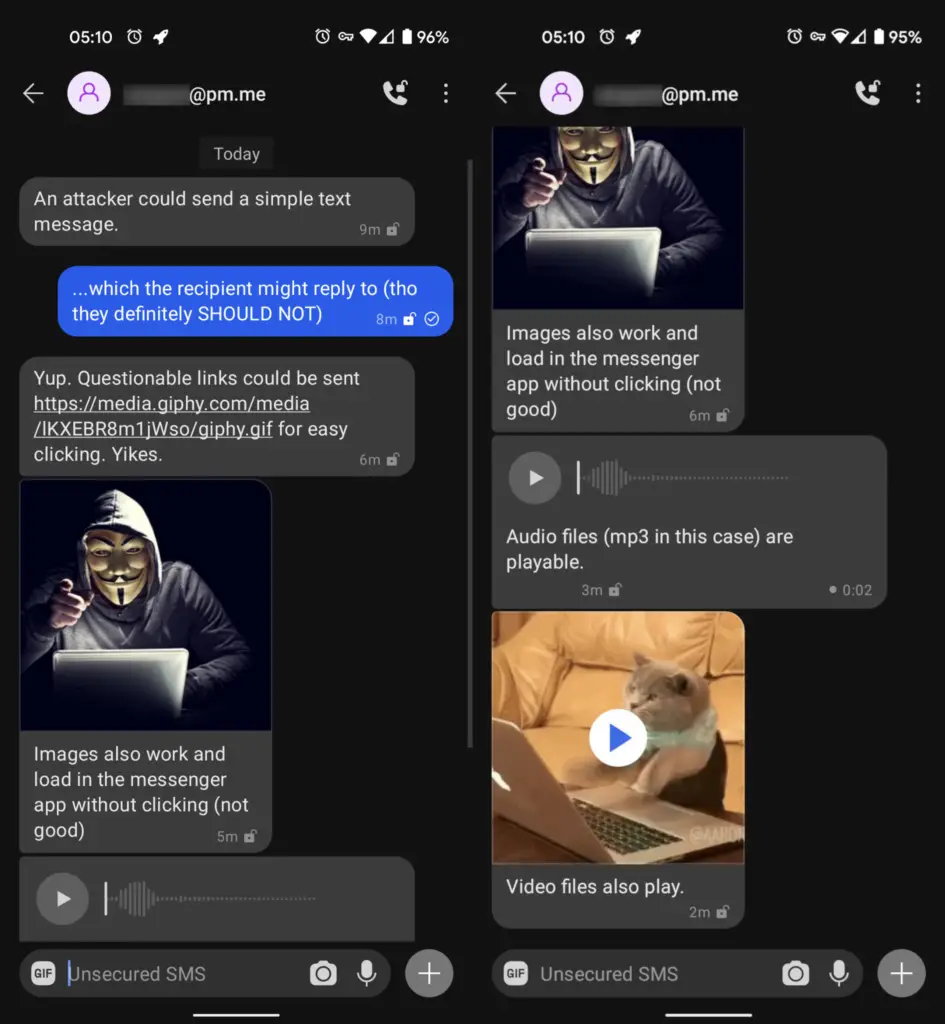
Hackers can easily exploit this service to send an anonymous text message. For example, an attacker could
Connect to the tor network
Open a temporary email account at a privacy respecting provider
Send some messages to one or more email-to-text gateways
Close the disposable email account
The recipients receive insecure SMS/MMS messages. While an emailed text message looks quite different, a user may act on the phish exposing their device and data to the attack through lack of knowledge and curiosity.
| Read this article detailing the dangers of MMS messages and what to do about them. |