I know, I know, you're probably thinking, "Why care about Bluetooth security on my Android? I just want to stream music to my speakers, connect my Air Pods, or control my smart home." But, there are security risks to be aware of when using Bluetooth on your Android device.
Hackers can access an Android device by compromising the Bluetooth devices connected to it. Once they have control of these devices, they can then bypass Android's protections and control apps, stealing sensitive information.
Nowadays, we use our mobile devices for everything from online banking to social media, and we store a lot of sensitive information on these devices. So, it's essential to understand the potential security risks associated with using Bluetooth technology on Android devices and mitigate these risks.

Android OS and Bluetooth
Bluetooth is everywhere nowadays, with over 4.7 billion devices using it every day. There are two main types of Bluetooth: Classic and Low Energy (BLE). They're like two peas in a pod, providing a short-range wireless connection between your Android device and your favorite peripherals.
Bluetooth classic is great for power-hungry devices like speakers, while BLE is like a marathon runner, conserving energy for your smartwatch and other low-power devices.
Communication between your Android device and your favorite Bluetooth device is possible thanks to the implementation of the Bluetooth stack on the Android operating system. You might wonder, "What the heck is a Bluetooth stack?" Well, think of it as a multi-layered cake (yum!), each layer responsible for a specific function.
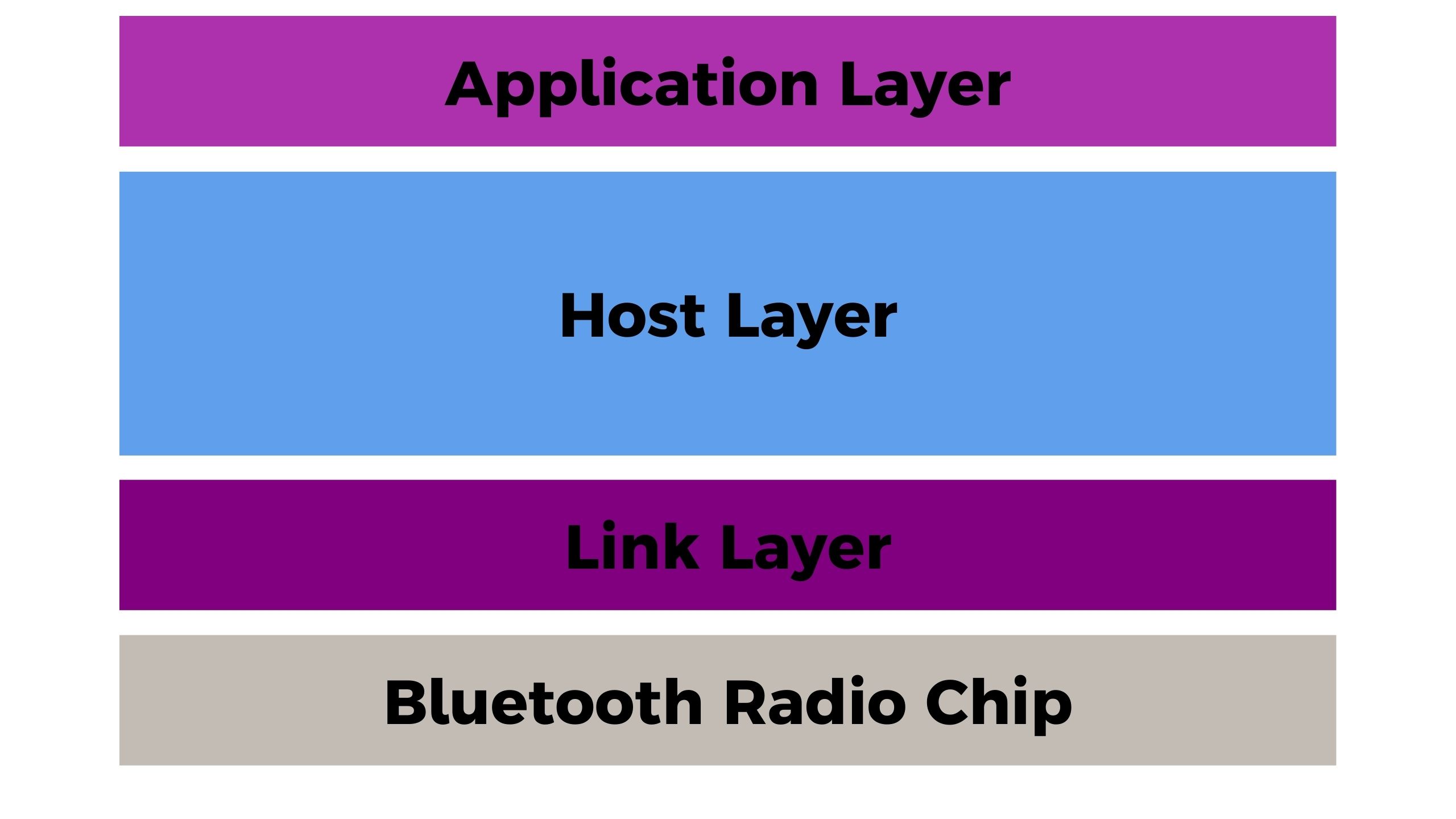
Abstracted Bluetooth Protocol Stack
At the bottom of the stack, we have the physical layer. This is where the physical Bluetooth components, like the antenna and radio, live.
Then we move up to the link layer, where the Bluetooth protocol is implemented to establish and manage connections between devices. Above that, the host layer manages Bluetooth device discovery and security.
Finally, at the top of the stack, we have the application layer, which is where all the Bluetooth magic happens. This is where apps can access Bluetooth functionality to communicate with Bluetooth peripherals, like speakers, headphones, or fitness trackers.
When it comes to connecting to a Bluetooth peripheral, a specific process takes place.
First, the Android device scans for available Bluetooth devices. Once it finds the device it wants to connect to, it sends a connection request. The peripheral then responds, and if everything goes well, the devices are paired.
Pairing is basically like exchanging secret handshakes to establish a secure connection. This involves exchanging encryption keys, verifying identities, and other fancy cryptographic stuff that's too complicated for us mere mortals to understand.
Once the devices are paired, they can communicate using a variety of Bluetooth profiles, which are like sets of rules that dictate how data should be transmitted and received for a specific application.
For example, there's the A2DP profile for streaming high-quality audio and the HID profile for connecting input devices like keyboards and mice.
Of course, with great power (Bluetooth connectivity) comes great responsibility, such as being aware of the security risks associated with using Bluetooth on your Android-based smartphone.

Potential Security Risks Associated with using Bluetooth on an Android Smartphone
Here's the thing about security on your Android device. It's like a chain and is only as secure as the weakest link. Unfortunately, most Bluetooth peripherals are that weak link. They're often made on a shoestring budget, and security is the last thing on their mind.
So, when you pair your Android phone with a Bluetooth gadget, the hacker won't go straight for your phone. Instead, they'll go after the Bluetooth peripheral and use it to get to your precious smartphone. Sneaky, huh?
But wait, it gets worse. Those Bluetooth devices could have been hacked by the previous owner, the seller, or even during shipping.
If the hacker succeeds in their evil plan, they could bypass Android's protections like permissions and isolations, get into your phone and wreak havoc. We're talking about controlling your apps, changing your security settings, and stealing sensitive information. Yikes!
So, what vulnerabilities can turn your Bluetooth peripherals into enemies?
The first one is related to the Bluetooth profile.

Bluetooth Profile
There's a problem with the current Android OS. It assumes that a Bluetooth gadget it connects with can only support a fixed set of profiles. But, according to a paper called "Breaking Android security mechanisms using malicious Bluetooth peripherals," that's not always true.
The paper explains that a compromised or hacked Bluetooth gadget can actually change its claimed profiles dynamically after pairing with an Android smartphone.
Such a device could first pair with the Android smartphone using a benign profile but then switch to another profile and start stealing information after pairing. And since it's already paired with your phone, you won't even know it's happening.
It's not just talk either. The researchers in the paper showed how they could take a Bluetooth headset and inject it with malicious code. The Bluetooth headset starts by advertising itself as a headset, and then, after it pairs with an Android phone, it changed its profile to the Human Interface Device (HID) profile and started sending unauthorized keystrokes to the phone.
A quick side note:
The Human Interface Device (HID) Profile is a Bluetooth profile that enables Bluetooth devices to communicate with human interface devices such as keyboards, mice, game controllers, and other input devices.
The HID profile allows these devices to exchange data such as keystrokes, button presses, and pointer movements between the input device and the host device. This means that a user can connect a Bluetooth-enabled keyboard, mouse, or game controller to a computer or mobile device and use it as if it were directly connected to the device.
The second vulnerability is related to the old pairing methods.
Legacy Pairing Methods
Bluetooth gadgets that still use the legacy pairing method, such as the Just Works method, can leave them vulnerable to spoofing attacks because they have no way of authenticating themselves**.**
A spoofing attack is when a hacker pretends to be a trusted device and tricks your phone into accepting data from them.
An example, if a fitness tracker uses the "Just Works" pairing method to pair with a smartphone. A hacker can easily impersonate it and start sending incorrect information to the associated app running on your Android-based device.
Other attacks that legacy pairing methods expose your device to are passive eavesdropping and man-in-the-middle attacks.
The last vulnerability concerns the incorrect implementation of the Bluetooth stack on the Android OS.
Logic Bugs
Bluetooth connections between paired devices can sometimes drop, and the devices must reconnect. The Bluetooth specification states how those devices should reconnect. There are two ways to do this: one is called reactive reconnection, and the other is called proactive reconnection.
Researchers in a recent paper found that the way Android phones do proactive reconnection is not quite right. The Bluetooth specification says that if the encryption process fails during the reconnection, the phone should either try to connect again or give up on the connection.
But on Android phones, when the encryption process fails during the reconnection, the phone just keeps talking to the other device in plaintext without trying to start the pairing process again to ensure the connection is secure.
Sharing data in plaintext without encrypting it is not secure and could allow an attacker to trick the Android phone into accepting fake data. The attacker could pretend to be the device that the phone was supposed to connect to and then send fake data to the phone. Without encryption, the data are not authenticated so there is no way for the smartphone to know if the data is coming from the right source.
Researchers have even tested this with the Oura ring and an Android smartphone.
In their experiment, the Oura ring pairs with the Android-based smartphone, and the researchers jam their connection to force them to reconnect. During reconnection, the attacker pretends to be the Oura ring, rejects encryption requests from the phone, and then sends fake data to the Oura app on the smartphone.
Final Thoughts
It's essential to be aware of the vulnerabilities in the Bluetooth system that can affect the security of your Android phone and the devices it's paired with. While some of these vulnerabilities are beyond your control, there are steps you can take to reduce your risk.
One simple way to protect yourself is to turn off Bluetooth on your Android phone when you're not using it. This will prevent unauthorized devices from connecting to your phone and accessing your data.
Additionally, ensure that any peripheral devices you use the latest Bluetooth protocol versions. This will ensure they have the latest security features and are less vulnerable to attacks.