Strong passwords are the first line of defense. Someone who knows your account name and wants access to your information will start by breaking your passwords. However, many people still use laughably weak passwords. Here is a comparison of some 8-character passwords I've seen in use.
| Weak | Better | Memorable? |
|---|---|---|
| 12345678 | Ur#1nMb! | Yes, "you're number one in my book!" |
| password | PBtoB^2. | Yes, "please be there or be square." |
| qwerty12 | $R_T3b7o | Not Necessary (because it's in your password manager) |
You'll see from this handful of examples that strong passwords (even just eight characters long) contain both upper and lowercase characters, numbers, and special characters. They never include any dictionary terms or personal information. I have some more examples in the next section.
Strong 8-Character Password List (Inspire Your Password Strategy)
In a world where cyberattacks are becoming more common, it's essential to have strong and unique passwords for your online accounts.
For example, consider these strong 8-character password examples:
Fr13ND?y
E4M^ddMm
!L9trKuh
The above passwords are strong because they contain the following:
Are at least 8 alphanumeric characters
Are not based on personal information (PII)
Not a word in any language, slang, dialect, or jargon
Both Uppercase and lowercase letters (e.g., a–z, A–Z)
Base numbers and non-alphanumeric symbols (e.g., 0-9 !@#$%^&)
Critical Warning: Please do not use these particular passwords now that I’ve published them here on the Internet. Create your own variations or use a password generator
Although a strong password is essential, it is useless if you use it for more than one site. If one site is compromised and your password is leaked, all other accounts with the same password can also be compromised.
You will also need to store your password securely, like in a password manager or vault. Check out my Recommended Tech page for the best password managers. But the best free and open source (FOSS) option is Bitwarden, while a good company-supported selection is 1Password or Dashlane.
Think About This:
Let's assume I store my valuables in a large metal safe but leave the key on top. The safe would not be very secure. It isn't simply about the security of the safe; it's also about how effectively you safeguard the key.
Similarly, writing down a complex password and leaving it on your desk where anyone can see it isn't good.

The Best Way To Make Your Feeble 8-Character Password Robust
According to researcher Gorden, all complex passwords aim to be unlike any word, phrase, date, or other string with semantic content. However, a good password must be easy to remember to be helpful.
Entropy is a measure of how unpredictable a password is. The higher the entropy, the more difficult it is to guess the password.
Two things make a password's entropy — its length and its complexity. Passwords that look random and gibberish offer the most complexity. It's also best to use the longest password possible and max out the website's or account's password policy.
Note: Some corporate systems have a fine-grained password policy like Azure AD (Active Directory), which may restrict the types of characters you can use. It's generally okay to try several combinations until you successfully satisfy the requirements.
It's straightforward to construct a complex yet memorable password.
I use the first letter of each word of a favorite song, poem, quotation, personal goal, or other sources and substitute numbers and other characters.
Examples of Unique Passwords Inspired by Phrases
| Example | Strong | Inspiration |
|---|---|---|
| 2Bon2B!? | Yes | Quote – To be or not to be is the question |
| !R0^A8gs | Yes | Favorite Song – Rock of Ages |
| I2l!tpbb | Yes | Favorite sport – I too like to play baseball |
| MD1n!R | Yes | Pet's name – My dog's first name is Rex |
| MsPi@24y | Yes | Sister's name – My sister, Peg is 24 years old |
What is a Brute Force Attack & How Long Does it Take to Crack An 8-Character Password
A simple brute-force attack is the most basic attack used against a password. An attacker tries all possible combinations of letters, numbers, and symbols to find the correct password.
The hacker leverages an application that will attempt common character combinations until the whole password is found.
Brute-force attack on passwords with different combinations
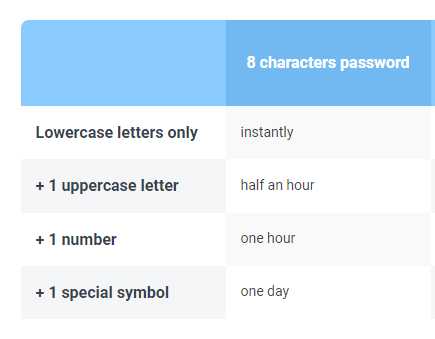
Source: How long does it take to crack an 8-character password?
To secure a password, you can add more characters or more than one uppercase letter, lowercase letter, number, or special character. The more of these, the merrier.
Which is More Secure? A Random Password Generator or Human-Generated Passwords?
There is no definitive answer to this question. Both methods have their pros and cons.
Random password generators create passwords that are difficult to crack because they are generated randomly and are unpredictable.
In the book The Basics of Digital Privacy, Author and researcher Derry Cherry states that password generators are close enough to random for the average person. Still, they aren't truly random because they use predictable algorithms within the software to create the password.
Password generator software is effective because the passwords it creates are based on computer device IDs and changing values such as the time of password creation. This allows for many passwords to be made in a short period while still being unpredictable.
However, the downside is that people often find it difficult to remember these passwords, especially if they are long and complex.
On the other hand, an analysis conducted by researchers revealed that humans rarely choose passwords that are both difficult to guess and easy to remember.
Human-generated passwords are easy to remember but can be cracked more easily than random passwords. The upside is that people are more likely to recall human-generated passwords without having to write them down or store them in a password manager.
I wrote detailed instructions on creating a memorable password using a password generator.

Weak 8-Character Password Examples (Strategies To Avoid)
Security analysts say that the length of a password is not the most important thing to worry about. The guessability of a password is a more critical factor. Easy-to-guess passwords are the easiest to crack. Please stay away from them.
According to this study, poor, weak passwords have the following traits:
The password is shorter than eight characters long
The password is a word in a dictionary (English or foreign)
Names of family members, pets, friends, coworkers, fictional characters, and so on
Computer terms and names, commands, websites, businesses, hardware, and software
The words "Sanjose," "Safran," or any derivative thereof
Personal information, such as your birthday and addresses and phone numbers
Word or number patterns like aaabbb, qwerty, zyxwvuts, 123321, etc.
Any of the above spelled backward
Any of the above preceded or followed by a digit (e.g., secret1, 1secret)
Stay Away from a Default Password
Using default accounts and passwords is dangerous, and many still do this out of convenience. A quick search on the web will provide most default passwords.
Stay Away From Common Passwords
Hackers often use lists of common passwords to try to guess the passwords for other people's accounts. If your password is one of the most commonly used passwords, then it's more likely that a hacker will be able to guess it and gain access to your account.
🛑 NEVER Use This List of Popular 8-Character Passwords
password
12345678 (a ridiculous 8 digit password)
iloveyou
sunshine
football
princess
trustno1
superman
1q2w3e4r
Stay Away From Passwords That Contain Words Appearing In Any Dictionary
Passwords that contain dictionary words are vulnerable to dictionary attacks.
A dictionary attack is a password-cracking technique that relies on a list of words. Dictionary attacks initially used words found in dictionaries, hence "dictionary attack."
The attacker tries to log in to the system using each word in the wordlist until they find a match. Dictionary attacks are often successful because many people use easy-to-remember passwords found in a dictionary.
Examples Of 8-Character Passwords With Dictionary Words
youmoron
whatever
Router66
changeme
justdoit
Stay Away From Passwords Containing Personal Information
People who know you or have access to information about you can guess your passwords. Your significant other's name, child's name, pet's name, birth date, phone number, or favorite sports team are examples of information that someone could use to guess your password.
List of 8-character Passwords Examples Containing Personal Information
august15
rosebud7
Natalie1
John&Mae
CHRISTINA
Having strong and unique passwords is vital to protect your personal information online in today's world. While we want to think of the Internet as a beautiful, calm place where everyone gets along, the truth is that it is more akin to the Wild West than a serene place.
Many people want to take your money and identity. Take proactive steps to protect yourself online.
How do your passwords stack up against my SIMPLE password checklist?