No one shows you this unconventional way of creating an almost unbreakable password. It’s the key to having a secure password to lock out hackers. So, what is an example of a strong password?
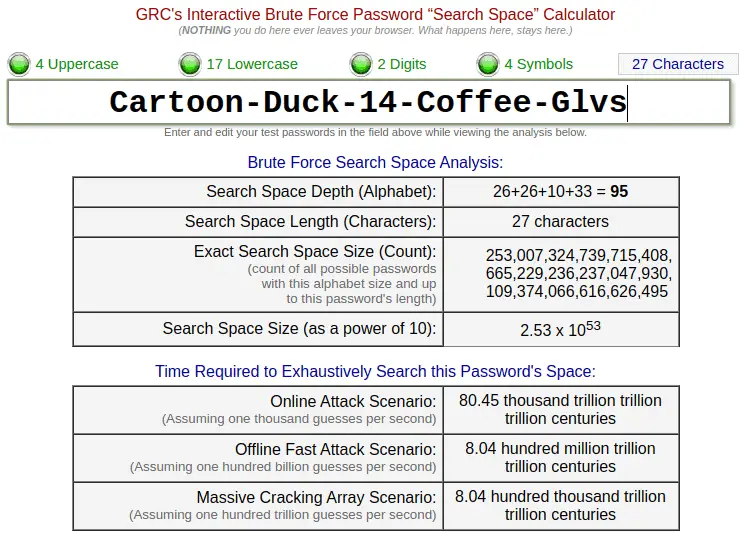
An example of a strong password is "Cartoon-Duck-14-Coffee-Glvs". It is long and contains uppercase and lowercase letters, numbers, and special characters. It is a unique password created by a random password generator. Strong passwords can be remembered, but should not contain personal information.
Cartoon-Duck-14-Coffee-Glvs is my password sample. Please don't use it now that I've published it here. Let's breakdown why this is a strong password example and how you can make something similar.
Strong Password Example: Breaking Down the Components
When it comes to crafting a strong password, there are three key elements to keep in mind: length, complexity, and unpredictability.
Length
The longer the password, the more secure it is. Aim for a minimum of 12 characters. Each additional character exponentially increases the time it would take for a brute-force attack to crack it.
Complexity
Incorporate a mix of upper and lower case letters, numbers, and special characters. This makes it difficult for attackers to guess your password using dictionary or rainbow table attacks. For instance, instead of using password, use something like 2023P@ssW0rD!.
Note: Yes, including the year in a password can help gauge when it's time to update an old password.
Unpredictability
Don't use easily guessable information like your birthdate, name, or common words. Combine unrelated words and characters to create a unique combination.
Now let's dissect a strong password: Cartoon-Duck-14-Coffee-Glvs.
It's 27 characters long, which is above the recommended 12 characters.
It includes upper and lower case letters, numbers, and special characters, meeting the complexity criteria.
It doesn't contain any predictable sequences or personal information, making it an excellent strong password example.
So, you know what makes a password strong, but how can you create one that's both secure and easy to remember? Let's dive into five tips that make this seemingly tricky task a breeze.
5 Tips to Create a Strong Password That's Easy to Remember
Simply remember these tips and you should be good to go:
1. Incorporate Personal Goals
This is a fun one. Add a personal goal along with a target year to your passphrase. For example, In 2024, run a 5K! or Buy Home In 2026.. This makes your passphrase memorable and serves as a daily reminder of your goals.
2. Opt for Length Over Complexity
A longer passphrase is often better than a short but complex password. Consider using a passphrase like I *$ Coffee Every 3rd Day. instead of ILv*$e3D. Believe it or not, the first option is actually more secure and way easier to remember.
3. Use Password Manager Instead of Your Brain
As secure as your passphrase may be, it's challenging to remember multiple strong passphrases for different accounts. Use a password manager like Bitwarden to store and generate strong passwords. This way, you only need to remember one super-strong passphrase to unlock your manager.
4. Passwords Suck Alone: Always Use 2FA
Two-Factor Authentication (2FA) or Multi-Factor authentication (MFA) is your second line of defense. Even if someone guesses or cracks your password, they'd still need access to your second factor—like your phone—to get in. Always enable 2FA when it's an option.
5. Regularly Update, But Not Too Often
Don't fall into the trap of changing your passwords too frequently; that can actually lead to weaker passwords over time. Aim for updating your most important accounts (like your password manager) every 6–12 months, unless there's a reason to believe your account is compromised.
How Do You Create a Strong Password? A Simple Guide
1. Generate It (Through Password Generators)
Using your password generator words or even and AI tool like Chat GPT is a good starting block to find some words ideas for your passphrase.
Are you wondering if using a password generator is safe? I dug into some frequently asked questions and provided 13 tips about passwords that I didn't include in this article.
2. Enhance It (Making Words Into Phrases)
Enhance your password by adding your flare. Swap the word order or change a word or two, so you can form a mental image or story with the passphrase.
3. Store It (In Mental Images Or A Tool)
Our brains are designed to remember visuals and ordered events. Leverage this mental wiring to help you memorize the words in your strong password. This trick is one of the secrets used by the top competitors in the World Memory Championships.

In my duck example, I might add a mental logo to the coffee cup to recall that the password belongs to my Starbucks login.
Ultimately, we’ll use a password manager to store your passphrase.
4. Un-Dictionary It (To Stop Dictionary Attacks)
Basing passwords off words from any dictionary is a bad idea, which is item #3 in our 6-point password checklist.
Attackers run several tools that quickly try common words. This is called a dictionary attack.
Here’s how to fix the problem: In your passphrase, choose one of your words, first, second, last, whatever. Drop the vowels in the word in that position.
Going back to my duck example: I’ve made an iron-clad promise to myself that I will always modify the last dictionary word in every password I create.
My final example of a strong password is “Cartoon-Duck-14-Coffee-Glvs”. I have modified Gloves to Glvs. Promise kept.
5. Measure It (To Prevent A Brute Force Attack)
Test the password strength on HowSecureIsMyPassword, a service provided by the password manager Dashlane. You can also check if your new secure password is already hacked at HaveIBeenPwned, a site by security researcher Troy Hunt. The project collects and helps users identify passwords included in any data breach.
The Future Beyond Passwords
The security landscape is continually evolving, and traditional passwords may not be the be-all and end-all solution for long. There are several emerging technologies that aim to make authentication more secure, convenient, and efficient.
Passwordless Authentication
The idea behind passwordless authentication is to eliminate the need for a password altogether. Instead, you use something like a magic link sent to your email or a time-based one-time password (TOTP) sent to your mobile device. This method is often considered more secure than passwords, as there's nothing static that can be stolen or guessed. The downside is that you need to have secure access to your email or mobile device to make this work.
Biometric Authentication
Biometric authentication uses unique physical characteristics, such as fingerprints, facial recognition, or iris scans, to verify your identity. Your biometric data is extremely hard to forge, and it's convenient because you're always carrying your "authentication method" with you. The key concern here is the storage and handling of sensitive biometric data. If compromised, you can't change your fingerprints like you would a password.
Passkeys
Think of passkeys as a more advanced form of a PIN. Instead of a static number, a passkey can be dynamically generated and tied to a particular device or app. This makes it more secure than traditional passwords and even standard PINs because it changes every time you authenticate. The only requirement is that both the sending and receiving ends need to understand and support this dynamic key generation.
Behavioral Tracking
Another frontier in authentication is behavioral tracking, where machine learning algorithms analyze your typical behavior—like how you type or how you interact with a device—and flag any deviations as potential security risks. While this sounds like it’s straight out of a sci-fi movie, the technology is increasingly being considered as a supplement to existing authentication methods.
Shockingly-Fast Crack of Your Windows Password
Are you using Windows? Here's a prime example to consider Windows alternatives.
Kevin Mitnick is a computer security consultant, author, and convicted hacker. In this video (3m32s@2x), he uses a readily available hacking tool to crack a Windows password in about 30 seconds.
(I've fast-forwarded to the right spot)
Other Questions You Might Have
What is a brute-force attack?
A brute-force attack is a type of cyber-attack where an attacker tries every possible combination of characters to crack a password. This method is time-consuming and less effective against long, complex passwords.
What is a rainbow table attack?
A rainbow table attack involves precomputed tables for reversing cryptographic hash functions, which can be used to look up the plaintext password given its hash. This type of attack is less effective if the password system uses "salting" before hashing.
What does "salting" a password mean?
Salting involves adding random data, known as a "salt," to a password before hashing it. This technique makes it harder for attackers to use precomputed tables, like rainbow tables, to crack the password.
What is a dictionary attack?
A dictionary attack involves an attacker trying all the words in a predefined list or dictionary to crack a password. The effectiveness of this method is reduced if the password uses a mix of upper and lower case letters, numbers, and special characters.
Is it safe to use password recovery questions?
Password recovery questions can be a weak point in security if they involve easily discoverable information, like your mother's maiden name or the name of your first pet. For better security, make the answers to these questions as complex and unguessable as your passwords.