Tor and I2P both provide means for anonymous communication, but which is more secure? What are their major differences? Let's compare Tor and I2P to find out...
Tor and I2P both rely on routing data through multiple peers to render tracking virtually impossible. The main difference is their focus. Tor is optimized for anonymous browsing on the regular internet, while I2P is optimized for anonymous communication within its own network.
The main focus of each project is not the only difference between these two. Here's a comprehensive comparison table that summarizes the main differences between Tor and I2P.

Tor vs I2P Comparison Table
| Factor | Tor | I2P |
| Project’s Focus | Optimized to provide anonymity for regular internet usage | Optimized to provide anonymity for private services |
| Encryption | Onion | Garlic |
| User Base | Popular | Less popular |
| Documentation | Better | Not as good |
| (Uni/ Bi)directional | Bidirectional path | Unidirectional path |
| TCP/ UDP | Only TCP | Both TCP and UDP |
| Centralization | Not fully distributed | Fully distributed |
| Performance | Download speed/ bandwidth is higher and average latency is lower | Download speed/ bandwidth is lower and average latency is higher |
| Router Selection Criteria | Relies on user-reported bandwidth data | Profiling based on observed performance |
| Vulnerability to DoS | More | Less |
| Vulnerability to Tracking | More | Less |
| Congestion Control | Low because it uses circuit switching | Better because it uses packet switching |
| Software language | C | Java |
Main Focus of Project
Tor is focused on providing anonymous access to the regular internet, while I2P is focused on providing hidden services - that is, websites that are only accessible through the I2P network and are not accessible from the open internet.
In this way, Tor and I2P are complementary projects: Tor mainly provides anonymity for regular internet usage, while I2P provides anonymity when you use hidden services on its own network.
Although you can still access the regular internet through I2P by using something called "out-proxies," it is not recommended as it is not part of its formal function. Tor also provides private services known as "onion services," though this isn't its main function, and these services are slower than their counterparts in I2P.
Encryption
Tor uses onion encryption, while I2P uses garlic encryption. Both are types of layered encryption.
In onion encryption, the sender wraps the message in several layers of encryption, each one hiding the layer beneath. And as the message hops from one computer or node to another on its way to its destination, it is decrypted one layer at a time.
No single node knows the complete communicating path; each node in the transmission path is only aware of the node it will get the message from and the next node it is going to send the message to.
Garlic encryption is a type of onion encryption that adds the ability to encrypt multiple messages that will be sent down different paths into one message. The multiple messages that are going to be bundled together are known as "garlic cloves or bulbs." The combined message is known as the "garlic message." So, a single garlic message may have more than one message for different recipients.
User Base
Tor is almost the de facto standard for anonymity online. It is more well-known and has a larger user base spread across the globe. It is well-documented and has a large number of developers, some of whom are paid to work on it.
I2P is less popular and has fewer users, the majority of whom are based in Europe. Its documentation isn't as good as Tor's, and it doesn't get nearly as much funding.
TCP /UDP
Tor uses the Socket Secure (SOCKS) interface. This allows it to work with nearly every web browser. However, because SOCKS can only send messages over TCP, this also limits Tor. It can only send messages over TCP.
I2P does not use SOCKS. This gives it the choice between UDP and TCP, which makes it perform better with certain applications. But without the SOCKS interface, most applications need to be changed a lot or made from scratch to work with the I2P network.
Unidirectional / Bidirectional
On the Tor network, the virtual communication pathways, also known as circuits, are bidirectional and facilitate two-way conversations between nodes.
In contrast, I2P's virtual communication path, also known as a tunnel, is unidirectional. And so, each node in the network has two tunnels, one dedicated to sending messages and one for receiving them, and a minimum of four tunnels are needed for round-trip communication between two users.
I2P requires more nodes during transmission than Tor but simplifies algorithms because each path is solely responsible for communication in one direction. This makes data delivery more flexible and reliable.
Centralization
Tor isn't as fully distributed as I2P. It has authorized directories in the US and Europe that it uses to store and distribute information about the nodes in the network. Anonymity is jeopardized if the directory server is compromised.
However, in I2P such centralization doesn’t exist. All the nodes in I2P form a distributed database where each participating node stores a list of nodes local to it.
Performance
This research paper examined the performance of Tor and I2P when accessing web pages and receiving files from a fixed location. The study found that Tor was superior in both latency and download speed when compared to I2P, with an average latency of 105.42ms for Tor versus 116.17ms for I2P. Additionally, a comparison of download bandwidth showed Tor to be 17% faster than I2P.
Router Selection Criteria
Both Tor and I2P are volunteer communities that rely on global volunteers to provide their bandwidth and computer resources in order to facilitate anonymous communication. Both networks use different selection criteria for which computers will be routers, as they try to ensure the best performance for their services.
Tor relies on user-reported bandwidth data when choosing its routers, which can be self-advertised or exaggerated by users.
Alternatively, I2P employs a more reliable system when selecting its routers. Participating nodes are profiled based on observed performance rather than claimed performance data in order to reduce misinformation and inaccurate reporting.
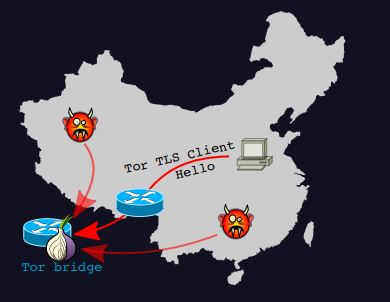
Attack on Tor. Image Courtesy of "How the great firewall of China is blocking Tor."
Vulnerabilities to Attacks: DoS ,Tracking
Because of its larger size, Tor is more susceptible to blocking and Denial of Service (DoS) attacks. Conversely, I2P's smaller size makes it less vulnerable to these types of attacks.
Also in Tor, the first router in a circuit knows the IP address of the person sending a message, and the last router knows the IP address of the person receiving the message. If both of these routers are malicious, it could mean that the anonymity of communicating parties is at risk. That's why it's important for Tor's node selection algorithm to select trustworthy entry guards.
In contrast, in I2P, this risk is reduced because even the first node does not know if it is forwarding the message to another peer that is part of the tunnel or the actual sender.
Congestion Control
The Tor network is susceptible to congestion because it uses circuit switching instead of packet switching.
Circuit switching requires the route to be set up before data transmission can begin, and it dedicates an entire circuit for the duration of the transmission, so it is less flexible in adapting to changing network conditions.
I2P, on the other hand, uses packet switching instead of circuit switching making it more resistant to congestion.
Packet switching works by breaking down data into much smaller segments, or 'packets', and sending them down separate routes. As packets travel through the network, they can take different paths based on their specific needs and have greater flexibility when it comes to avoiding traffic jams or heavily congested areas on a network.
At the heart of any anonymous communication system is a random routing path. Image courtesy of How Do Tor Users Interact with Onion Services?
Anonymous Communication Systems
Communication on the internet is not anonymous. Your IP address is a telltale sign that identifies you and can be seen by anyone monitoring the traffic, even if your messages are encrypted.
This sounds like a scary privacy problem, especially when researchers have found that big companies like Target can predict when you're sick or pregnant with just your data; Facebook can predict your sexual orientation, even if you don't explicitly share that information, and Google can predict when we want to search.
This begs the question: Why wouldn't anyone want their identity hidden in such an intrusive climate?
An Anonymous communication system (ACS) is an attempt to prevent such tracking and online surveillance. An ACS is made up of multiple nodes/routers/relays that form an overlay network. This means that when you send a message, it passes through multiple nodes in a random routing path making it difficult to say who the sender is.
Benefits of ACS:
Makes traffic analysis hard: By passing messages through multiple nodes in random routes, surveillance and monitoring by third parties such as internet service providers (ISPs) is virtually impossible.
Prevents correlations: Because different messages take different paths, it is harder to tie a certain message back to its sender or receiver. It is difficult to see the linkability between two communicating devices
Prevents tracking: It hides the identities of the communicating parties, even from each other.
Popular examples of anonymous communication networks are Tor (The onion routing network), I2P (Invisible Internet Project), JAP (Java Anon Proxy), Freenet, and Mute.
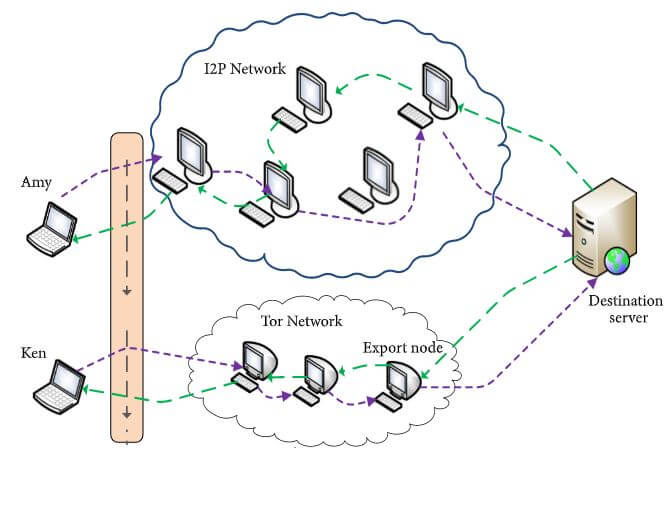
How Tor and I2P work. Image Courtesy of MSFA on IoT anonymous communication systems
What Is Tor and How Does It Work?
Tor is an open-source, encrypted, anonymous communication system that lets users stay private and anonymous online.
The Tor network system relies on members of the network to volunteer their machines, which will then be used to form a virtual communication path, called a "circuit," between nodes on the network.
The circuit is made up of three nodes, or relays, that are chosen at random.
The first node on the circuit is known as the "entry guard," and it will know the IP address of the actual sender but not of the destination. The second relay is known as the "middle relay." The last relay, referred to as the "exit node," will know who your destination is but not the sender's IP address.
When a user wants to send a message through Tor, the data is broken down into small segments called cells, and then each cell is encrypted multiple times in a series of layers (hence why it’s known as "onion routing"). As the cells travel through the network, each node on the circuit decrypts one layer of encryption and then sends it to the next node in the circuit.
Because each node in the circuit only knows about the previous and next relay, no single node can know the entire circuit path. This ensures that at any given time, no single node knows both where the data originated from and who its final destination is, making it impossible to trace a message back to either a sender or receiver.
What Is I2P and How Does It Work?
The I2P network is another type of anonymous communication network. It is designed to allow users within the network to communicate and access information without revealing their identity or location.
Unlike Tor, I2P is a fully private network whose traffic is separate from that of the normal internet. It only has a few out proxies that interface with the public internet.
Like Tor, the I2P network is formed by members who volunteer their machines as relays. These participating machines are called peers, clients, nodes, or routers. Each peer runs a piece of I2P software that is responsible for creating, managing, and routing the I2P tunnels.
An I2P tunnel is a virtual routing path for transmitting messages between nodes. The I2P tunnel is unidirectional, that is, it can only be used in one direction, and so each peer in the network has two tunnels: an inbound tunnel and an outbound tunnel. The inbound tunnel is used for receiving messages from other peers, while the outbound tunnel is used for sending messages to other peers.
Each peer can choose how many peers make up their tunnel, allowing them to control how anonymous their communication is. The more peers in the tunnel, the longer the length and therefore the higher the anonymity, but the lower the speed of transmission.
I2P also uses layered encryption similar to Tor's onion encryption, but it takes things one step further by allowing multiple messages that have different destinations to be encrypted into one message. This is known as "garlic" encryption. Therefore, a single garlic message can contain multiple messages for different recipients.
This makes it impossible to find out where a message came from or who sent it. This gives users a high level of privacy and anonymity.
Final Thoughts
Both Tor and I2P are excellent tools for staying anonymous online. However, sometimes knowing where to start can be challenging.
Fortunately, there is an offering from LinkedIn Learning about learning Tor & the Dark Web that might address that concern. Mike Chapple, the instructor of this course, does a great job at explaining how Tor works, as well as suggesting proactive steps for secure online communication.
Whether you're a seasoned tech veteran or just starting out exploring alternative network options, this course provides clear guidance. Don't forget to sign up for Mike's course, if staying anonymous online is your main priority.