Did you accidentally click a suspicious link from an email or text? It's pretty common to tap a link or button reflexively, with around 40% of emails globally being spam and the average American receiving 14 unsolicited SMS texts per month. Here's what usually happens when you open a phishing link.
After clicking a phishing link, the sender knows you are a valid target. The attacker receives basic data like approximate location, device statistics, and any information voluntarily provided. A phishing link may download malware. Users should take precautionary measures.
So if the sender gets this information, what are the immediate risks to your phone computer and data?

What Happens When You Accidentally Click on a Spam Link: Immediate Risks
When you click on a spam link, you're usually directed to another location on the web, sometimes via a chain of 2–3 redirects. This redirection chain is often used to mask the final destination, making it harder for security tools to identify and block the malicious website.
The primary goal of the person behind the spam link is typically financial gain. They generally aim to collect personal or financial information from you, commonly through a tactic known as phishing. Phishing involves a website that mimics a well-known service to trick you into entering sensitive information like usernames and passwords. The risks here can range from identity theft to unauthorized financial transactions.
Another intent could be to install malware on your system. This is more sinister, as the attacker is not just collecting information but gaining a level of control over your device. Once malware is installed, your computer could serve as a launchpad for attacking other systems or spreading the malware further.
If you're on a smartphone, you're mainly better protected against such threats, particularly if you keep your operating system and apps updated. Mobile operating systems are designed with more robust, built-in security measures.
On the other hand, laptops and desktops, especially those running older versions of operating systems, are more susceptible to these kinds of attacks. Mac and Linux systems tend to be more secure because of their Unix-based architecture, which offers stronger built-in security features compared to others.
What I Do:
Pause for 2 seconds and truly read the context around links and the web address (URL) that you will be directed to.
Android Users: I use URLCheck. Install it from Google Play, F-Droid, or directly (what I do) from the source repo, which acts as a browser and helps you inspect URLs before opening them.
Remember, the best line of defense is always caution, awareness, and prevention
So, if desktops and laptops are more likely to be hacked, what about your Android or iPhone? Do you even need to worry about them?
Can Your iPhone or Android Smartphone Get Hacked by Clicking on a Link? Myths and Facts
Let's tackle some myths and facts about the security of iPhones and Androids, especially when it comes to clicking on spam or phishing links.
Myth 1: Smartphones Are Immune to Phishing Attacks
Fact: Smartphones are vulnerable to different types of advanced phishing.
Many people think that smartphones are somehow magically immune to phishing attacks. That's not entirely the case.
Just like laptops and desktops, smartphones can be compromised if you click on a malicious link.
Phishing attacks actually happen more often now that smartphones are more prevalent than laptop or desktop computers. These devices are often more affordable and accessible to a wider set of people, including those that are less tech-savvy.
Attackers are becoming increasingly creative in their methods, especially when targeting mobile devices. And yes, while smartphones are more hardened than laptops or desktops, ultimately it's the human user that is susceptible to phishing attacks.
Be cautious with all links you receive, no matter the device you're using.
Myth 2: Legitimate-looking Links Are Safe to Click
Fact: Scammers often disguise malicious links to appear legitimate.
A link may look like it's from your bank, a trusted retailer, or even a friend, but that doesn't make it safe.
Scammers have become highly skilled at creating links that appear trustworthy.
They can clone websites and even make the URL look almost identical to the real thing. Always double-check the URL and, if in doubt, go directly to the website by typing it into your browser rather than clicking the link.
Myth 3: My Smartphone Will Warn Me If a Link is Dangerous
Fact: Built-in security features may not catch all malicious links.
While it's true that both Android and iPhones have certain security features designed to flag dangerous sites or downloads, these systems are not foolproof.
Cybercriminals are continually updating their tactics to bypass security measures. Therefore, you should never rely solely on your phone's built-in security features to keep you safe.
Myth 4: If Nothing Happens After I Click, I’m Safe
Fact: Malware can operate in the background without obvious symptoms.
You clicked a link, and nothing happened—no download, no request for personal information, nothing. You're safe, right? We'll no.
Some forms of malware are designed to operate silently in the background, collecting data or preparing for a larger attack. Even if it seems like nothing happened, it's essential to take immediate action to secure your device and personal information.
Alternatively, the link sender may have received some information just from clicking the link. As mentioned earlier, the attacker now knows you're a compliant target. Additionally, they may have received some basic location information and device specifications.
I will generally do a force reboot (not a factory reset) of my smartphone once a week. This can drop background processes that made it onto my device.
How Do I Know If I Clicked a Phishing Link? Indicators to Watch For
Unfortunately, there are no telltale signs that guarantee to indicate you've been infected by clicking on a fishing link. There are a few red flags that you can keep an eye on if you reflexively tap a link.
The URL in the Address Bar
First off, take a look at the URL in the address bar. Phishers often register domains that look very similar to legitimate ones, hoping to catch people off guard. For instance, they might use goggle.com instead of google.com, or change the domain to something like .net instead of .com.
Always verify the URL to make sure it's what you expect before interacting with a web page.
Asking for Sensitive Information
Another giveaway is when the site immediately asks you to input sensitive data such as your username, password, or financial information.
Legitimate websites that need this information will usually have a process that confirms your identity first, and they certainly won't ask for it out of the blue. Be extra cautious and skeptical when a website asks for this information without reason, especially when there's a sense of urgency to the wording.
SSL Certificate Warnings or Lack of HTTPS
Your web browser does a good job of alerting you to potentially unsafe websites by warning about SSL certificate issues or showing the site as "Not Secure".
If you see this, especially if you've been directed there from an email link or a pop-up, steer clear. Do not simply ignore this warning.
Poor Website Design
Lastly, check the overall quality of the website. Most phishing websites are hastily put together and may contain poor design elements, like misspellings or grammatical errors.
Legitimate companies put time and effort into their web design, including proofreading. If something feels off, trust your instincts.
These are some of the most immediate indicators that you may have landed on a phishing site. The key takeaway here is to be vigilant and double-check everything when something feels off.
So, what do phishing attempts actually look like in the wild? Here are some common examples and how to recognize them.
Common Phishing Examples: How to Recognize a Trap
When you receive an email or text message with a sense of urgency, like saying your account will be locked unless you act right away, be cautious.
Scammers use these tactics to instill fear and prompt immediate, thoughtless action. Always double-check with the company through a verified contact method before acting.
Another red flag is when you receive unsolicited requests for personal or financial information. Legitimate organizations usually won't ask you to send sensitive information like your social security number or bank details through email or text. If you ever encounter this, contact the organization directly through a known, trusted method to verify the request's authenticity.
Sometimes wording that is a bit "off" and isn't phrased in a way that is native or familiar to you is a sign that a phishing attempt is imminent. This is becoming less common of an indicator now that generative AI tools like ChatGPT. Scammers can use these tools to generate more believable phishing emails or texts.
Lastly, always scrutinize the sender's email address, especially for messages that claim to be from reputable organizations.
Scammers often use email addresses that look similar to, but not the same as, the companies they're pretending to represent. Check for subtle misspellings or extra characters that might indicate it’s not a legitimate sender.
By staying alert to these warning signs, you'll have a better chance of avoiding phishing traps and keeping your information secure.
Pop Quiz:
Take a look at this text I received. Study the message carefully. Can you identify the 5 suspicious parts that should set off alarms? Scroll below for the answers.
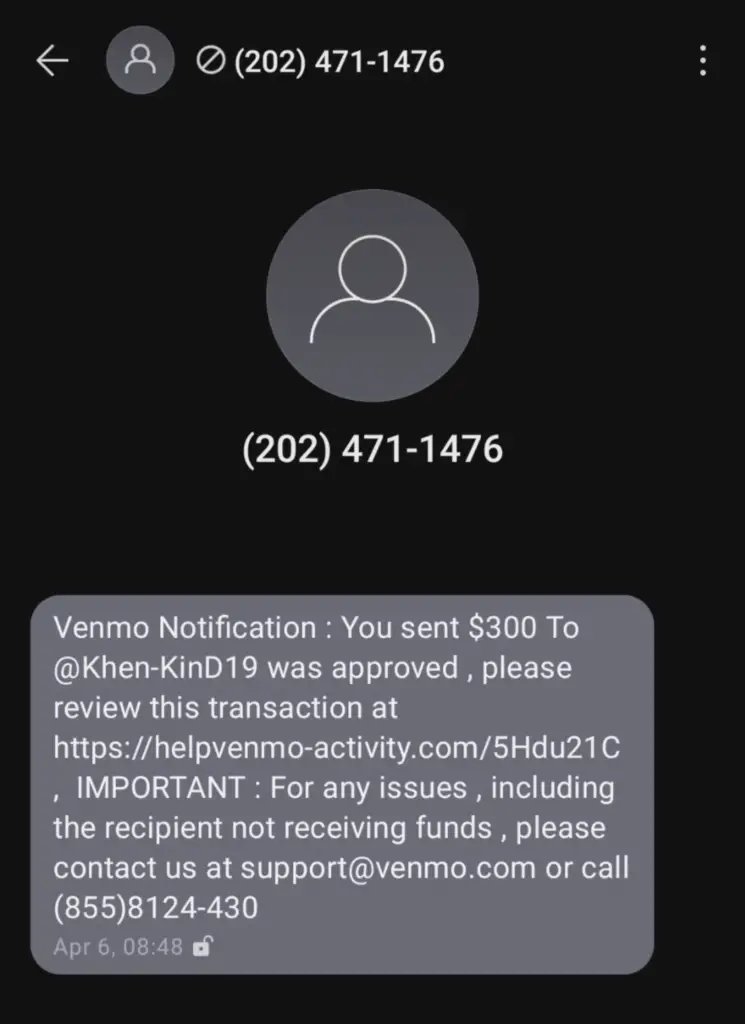
Hook: Many people would be worried about losing $300 unexpectedly.
Curiosity: We don't know who the user is, but the transaction was approved.
Urgency: "Venmo" wants you to review the "transaction" (picture me using air quotes) for any problems. The attacker legitimized the message by using the correct support email and phone.
Copy-Cat Link: The link has the word Venmo, but it's clearly not help.venmo.com (the correct URL).
Bad Formatting: Companies the size of Venmo ensure their notifications are well-formatted.
a. The grammar is incorrect.
b. The toll-free phone number has the dash incorrectly, not following the formatting of US or Canadian telephone numbers.
c. There are odd spaces before the commas and colons.
It's also possible that the text message originates from an out-of-service or disconnected phone number, which you shouldn't call back, of course.
But what if you've already fallen for one of these traps? Let's look at quick actions you can take to mitigate the damage.
Quick Actions to Take Right After You've Accidentally Clicked on a Phishing Link
First thing's first, disconnect from the internet immediately by putting your device on airplane mode. This will halt any ongoing data transmission to the malicious site, reducing the chances of further compromising your device or leaking personal information.
If the device you've clicked the link on is a work phone or computer, it's essential to notify your IT department right away. Use your personal phone or another device to email them or give them a call. The sooner they know, the quicker they can take steps to protect the company network and your device.
Another immediate action you can take is to search the subject and some email body in a search engine. This could reveal if the email is part of a known phishing campaign. If others have received the same email and flagged it as a scam, you'll find posts or articles warning about it.
Now, take some notes. Re-read the email and try to understand why you clicked the link in the first place. Was it the sense of urgency or maybe familiarity if it appeared to come from someone you know? If it's from a known contact or within your organization, reach out to them via a different method to confirm whether they really sent you that email.
Did clicking the link initiate a download? If yes, locate and delete the downloaded file from your device immediately. This could be an executable file containing malware.
Also, document whether you interacted with the website that the link led to. Did you enter any passwords, personal information, or upload files? This will be crucial information if you have to take further remedial steps.
Finally, hard reboot your device (NOT factory reset):
iPhone: To force restart an iPhone, quickly press and release the volume up button, followed by the volume down button, and then hold down the power button.
Android: To force reboot Android devices, hold the power button for 30 seconds (which is going to feel like a long time). Samsung phones require you to press and hold the volume down and power button for 10 seconds.
... Keep holding: For all smartphones, continue to hold the force restart until you see the phone's splash screen to appear before releasing.
I hard reboot my smarphone every week. I first checkt that an update is not in progress, but generally, I have not had any problems from doing this regularly.
But what if you could drastically reduce the chances of falling into the phishing trap in the first place? Let's delve into some strategies to help you become more scam-resistant.

Future-Proofing Against Scams: Strategies to Avoid Accidentally Clicking on Phishing Links Again
Being skeptical of all incoming emails and text messages should be your default mode.
Think of every message as guilty until proven innocent. When you're presented with a link or button, assume it's there to harm you until you can establish that it's not.
As I mentioned earlier, good practice is to count to 2 before allowing yourself to click or tap on a link. This momentary pause will give you time to evaluate whether you should proceed.
Then, before you click or tap that link or button, double-check the URL and the sender's email address. If you hover your mouse over the link without clicking (or long press on smartphones), most email clients and web browsers will show you where that link will take you.
Again, an app like URLCheck from earlier can really help with this type of inspection.
In the case of text messages, always be wary of shortened URLs and links that don't directly state where they're taking you.
Also, inspect the sender's email. Is it from a company you recognize? Is the domain name spelled correctly? Even a single letter off could be a red flag.
Educate yourself regularly on the latest phishing tactics and red flags. Scammers are constantly innovating, so your understanding needs to evolve too. Follow reputable cybersecurity blogs, participate in online forums, or even take short courses to update your knowledge. Being armed with the latest information puts you a step ahead in recognizing newer types of scams.
For those who are more technologically inclined, consider utilizing tools like an application firewall or DNS filtering services.
An application firewall monitors data as it travels to and from your device, providing an additional layer of security by blocking suspicious activity.
I use NextDNS which offers customizable DNS-level network filtering, allowing you to block known malicious websites and better control your online environment.

What are the types of phishing?
The types of phishing attacks grow as cybercriminals find new social engineering techniques, communication channels, and types of targets to attack.
Email phishing
Phishing emails are spam or fraudulent emails containing a malicious website phishing URL or attachments with embedded URLs. This is the most common communication channel due to the low cost of launching a campaign. However, spam filters are evolving to include AI and machine learning, allowing better identification and quarantining of suspicious emails.
I wrote a complete breakdown of what happens when you open a spam email that successfully got you to click on its link.
Vishing
Vishing is a call-based phishing attack that entices a target to expose confidential information to cybercriminals via a phone call. Vishing is usually more convincing but requires a highly researched target. It's one of the least used, with only 1% of the phishing attacks attributed to vishing.
Smishing
Smishing is a text message phishing link sent over SMS or secure messenger aimed at stealing personal or corporate confidential data from targets. Smishing victims usually receive deceptive text messages urging them to act urgently, sometimes from spoofed phone numbers.
Spear Phishing
This targeted attack on victims through emails or text containing plausibly accurate information on or around the target to manipulate the victim into action. The mark is usually driven more effectively due to the increased legitimacy of the message.
Whaling
Whaling is spear phishing a high-valued target, usually carried out against essential or high-ranking personnel of a target company.
The attackers may impersonate the top executive to lure a company's accountant or IT personnel into obeying specific instructions.
Whaling or CEO fraud is usually aimed at stealing sensitive information, accessing a corporate network, or defrauding the company.
Email forensics can be an effective tool for identifying and investigating phishing attacks, including spear phishing and whaling attempts