Here's how to hide your secure contacts from prying eyes, spammers, and big data companies.
Deny apps access to your smartphone's contacts list.
Move your sensitive contact records to separate storage.
Set up end-to-end encrypted contact synchronization.
Choose a low-tech or analog option.
Reduce the number of people and companies that have your information.
Help educate others.
I've personally found that contact lists are treated with less security than your email address despite being far more valuable. Sure, marketers send you junk mail, and companies leak your email address in data breaches. But your name, phone number, home address, and even birthday get uploaded to the internet without your permission and by the people who care about you the most: your friends and family.

You're Making a Big Mistake
While testing several messaging apps, I reviewed Snapchat, which required a phone number for registration. Then the app asked for permission to access my secure contacts list, which I denied. The final step involved linking to others' profiles. I was shocked.
Snapchat accurately listed people I know. How? Then it dawned on me. 💡
My friends and family allowed the app to copy their contacts list and upload it to Snapchat's servers. This included my phone number and likely my name, along with various other bits of my information.
I'd guess 90% or more of us make the mistake of allowing any app access to our contacts list.
I made this mistake too. Only a few months ago, while detoxing from Facebook, I allowed the app to synchronize my contacts with Facebook's servers. It took an hour to scrub my data off my account. I spent another few hours auditing other apps with contact list access.
How to Disable Contact Access for Apps on Android
Here's how to audit your contact list permissions on Android:
- Go to Settings and search for "permission"
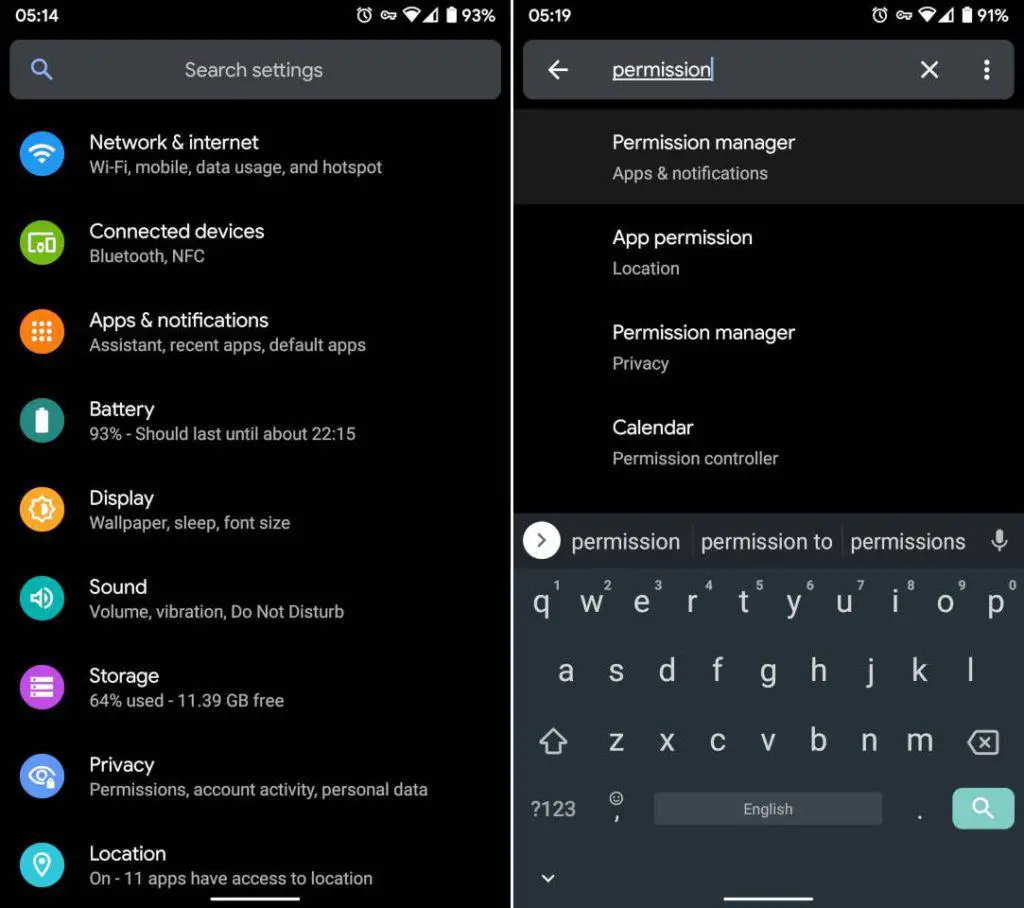
2. Tap a Permission Manager result, then launch Permission Manager
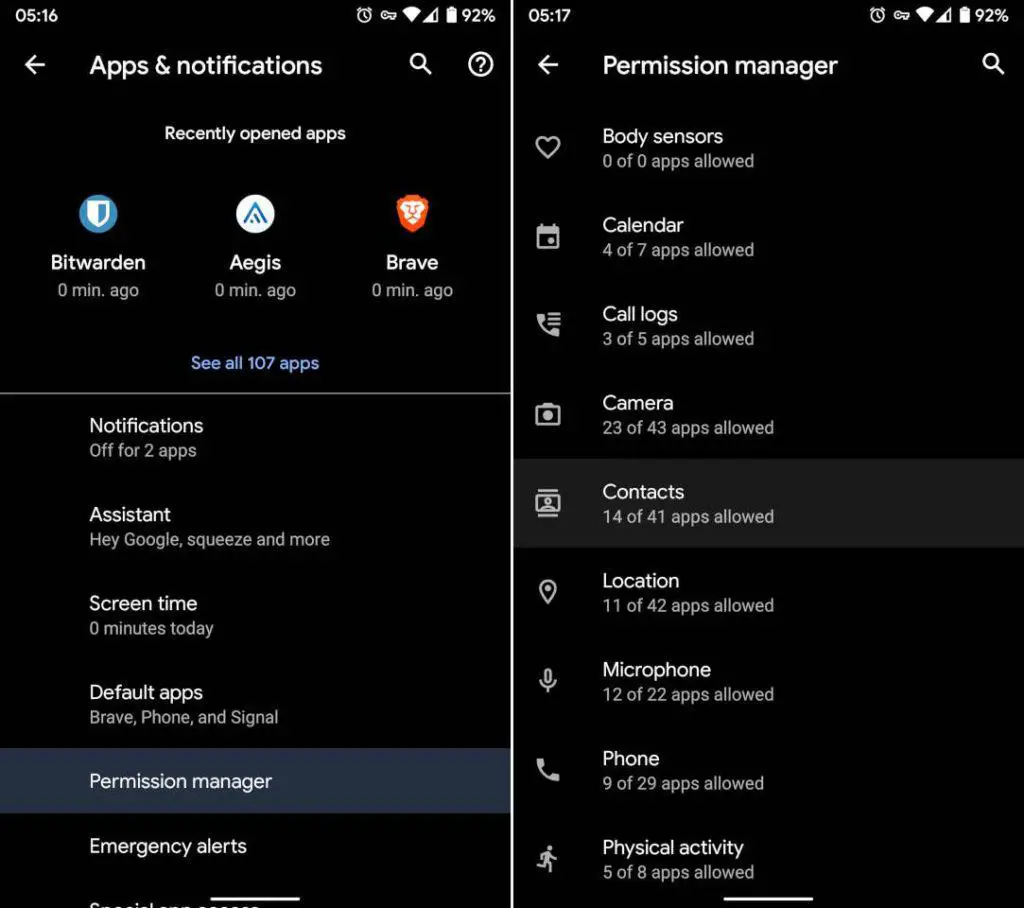
3. Tap the Contacts permission
4. Go through the "Allowed" list and switch to "Deny" any apps that do not need access to your contacts list to function. For example, as I'm taking screenshots, I've been denied access to my TTS engine, Keep Notes, Google Maps, and Google Translate. I'm allowing access to apps like Phone, Email, and messenger apps (e.g., Signal, Telegram)
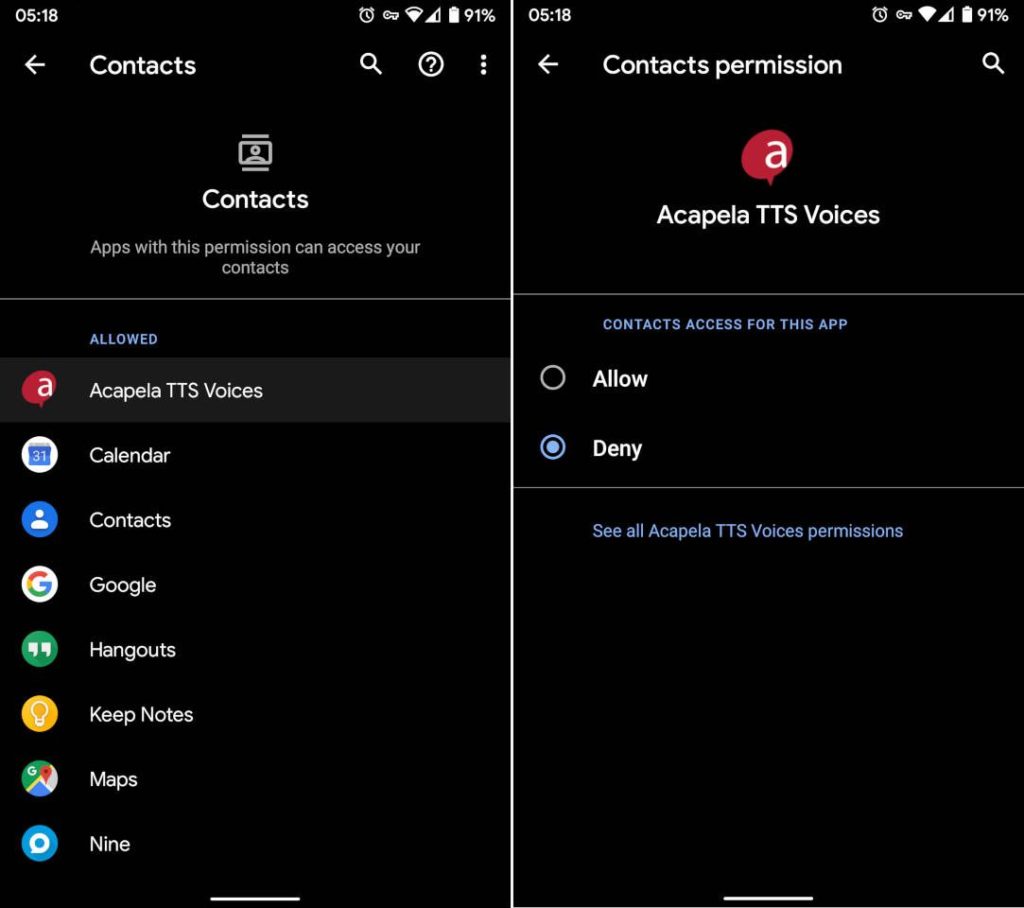
On Android, these steps might differ depending on your device. Some manufacturers modify Android on their devices so that the above settings might vary slightly for you.
For iOS users, the process is similar:
Go to Settings and scroll and tap on the Privacy option.
Tap Contacts.
Use the toggle on the right to deny access to Contacts for any apps that do not require permission to function.
Apology: Sorry to all my friends and family for giving Big Tech your information without asking first.
Now that we've taken an essential step to secure your Contacts, it looks like you have a double duty here:
You have to guard the contents of your contacts list to protect the privacy of your loved ones and business relationships and
You have to educate your contacts on how to help protect your privacy through proactive steps. ...or stop giving out your personal information.
Let's start by showing you how to hide, secure, and make your contacts private, which is the easier of the above two. Later, we'll go over simple measures to help others.
How Can You Hide a Contact?
We have three methods of hiding a contact in your contacts list.
Hide a contact in plain sight.
Make a contact invisible in your list.
Move a contact to a more-secure list.
In Plain Sight (Obfuscated Contacts)
The easiest way to hide a contact is in plain sight. By changing the first name, last name, company name, etc., you use the concept of security through obscurity. Here are some examples showing this quick way to hide a contact in your contacts book.
| Change This | To This | Concept |
|---|---|---|
| Cammie from the club | Dr. Cameron Ryan, DDS | Add title and/or formal credential; use a gender-ambiguous name if possible |
| Exclusive DUI Lawyers | Exclusive Financial Planning, LLC | Change the industry and add a company type for legitimacy |
| Robert Smith | Bob Smitty | Use shortened or nicknames |
Including a bit of the real name will help you remember the actual contact.
While you can change the names, a phone number or email address must remain accurate and cannot be altered. Security through obscurity might thwart the casual snooper and is not proper security which has been known since the mid-1800s.
“Rogues are very keen in their profession, and know already much more than we can teach them.”
Alfred Charles Hobbs, Locks and Safes, 1853, linked via The New York Times
Invisible In the List (Hidden Contacts)
The default contacts app on your smartphone is designed to help you find contacts quickly.
A few methods show how to use labels and groups to hide certain records from the list. These instructions are to help you stay organized and are not security- or privacy-focused steps.
Do not try to make your contacts app do something it wasn't designed to do. Removing sensitive or secret contacts from your primary contacts list is better.
Separate List (Compartmentalized Contacts)
Let's use a separate list to hide contact records from your primary Contacts app. This strategy is called compartmentalization.
I reviewed several note-taking apps, which are solid choices for storing a secondary list of contacts. You might also use a notes app that you already have installed. Select an app that is not specifically designed to manage contact records.
To improve your security, let's keep people and other apps from gaining access to your new secret secondary list.
How To Secure Your Contacts
Hold On!
Are you kidding me!?!? I just read this article from Wired. They reported that some people actually store sensitive data in their address books. 😖
Storing your passwords, social security numbers, PINs, health information, credit card numbers, etc., like this opens you to being hacked!
The average contacts app is very insecure. The data has no protections like access restrictions or encryption.
In fact, hackers do not even need a sneaky exploit. Third-party access to your contacts list is a feature of your smartphone's operating system on both Android and iOS.
Put sensitive data in a password manager, not your contacts list.
We have two options to upgrade from storing sensitive contacts in a secure notes app.
Use a privacy-centric email service with secure contact list handling.
Use a password manager to store contacts.
Stored Alongside Your Privacy-Focused Email Service
The website Privacy Guides offers an excellent list of email services, many of which include a secure address book.
For example, Disroot.org is built around a platform of tools "based on principles of freedom, privacy, federation, and decentralization." The toolset includes contact management through Nextcloud Contacts.
Another great choice from the list is the highly-respected ProtonMail which is well-known for its secure email.
The service includes ProtonMail Contacts which stores and walls off your private contacts list in the app. The free tier of ProtonMail allows for storing names and email addresses. A paid subscription gives you access to all the secure contact form fields, including phone numbers, addresses, and notes in their contact management.
This is the option I use to protect my contacts.
Locked Inside Your Password Manager
Everyone needs to use a password manager to store account logins. It's also an excellent place to keep your personal contacts.
For example, the free and open-source service, Bitwarden, includes a contact-type record providing plenty of fields for securing contacts.
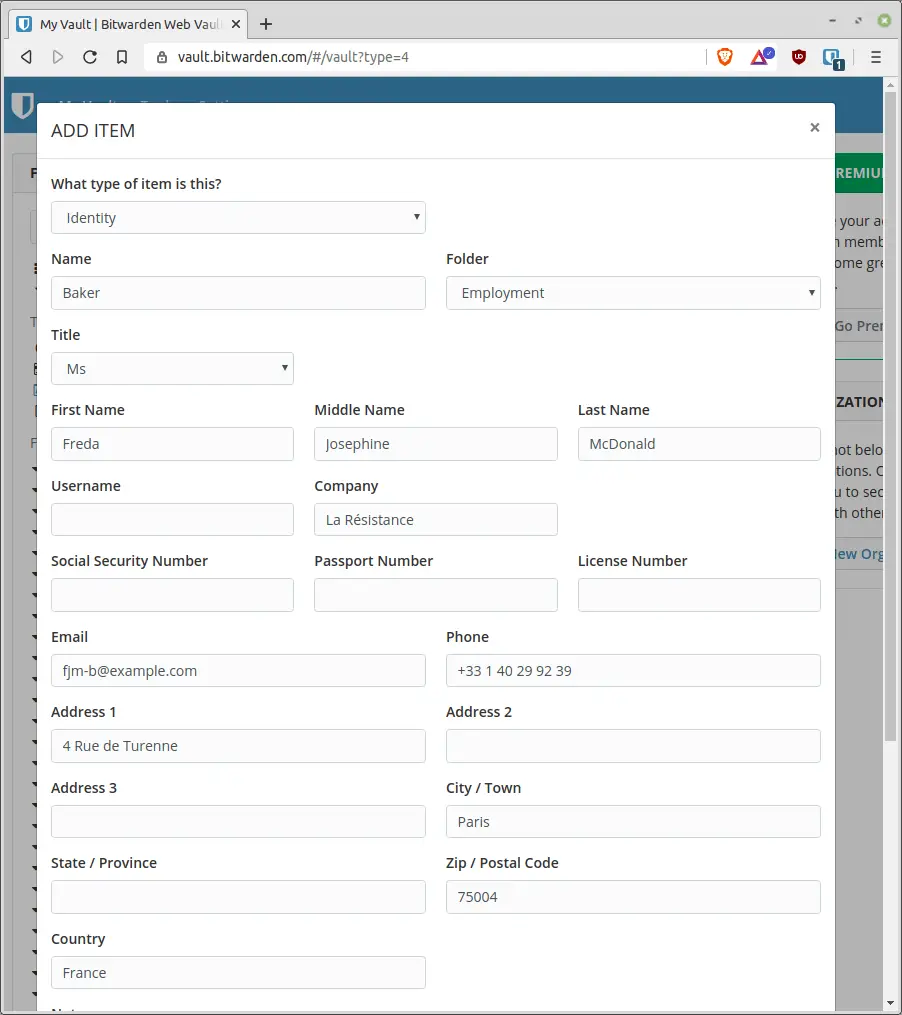
Most password managers offer a contact-type record, including the ability to auto-fill a contact form with the information. Other password vaults only include a free-form note option which will be fine for storing contact form data.
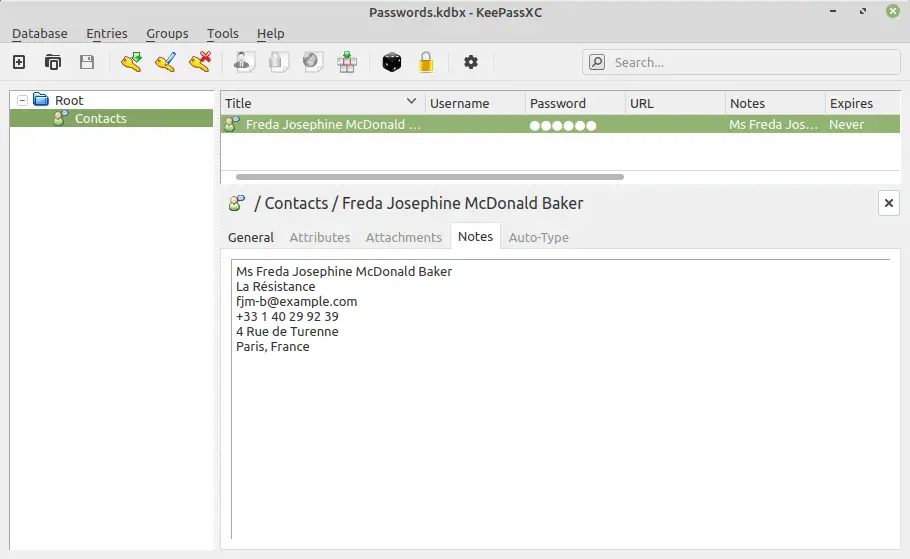
A password manager is the perfect double-duty utility to store your passwords and your secure contacts list. Many include organization through folders, categories, or tags. You can easily create a contacts folder within the secured vault.
Highest-Level for Private Contacts
Earlier, we discussed compartmentalization by keeping a secondary, private list of contacts on your primary phone. We can take this concept further by moving your secure contacts completely off your primary device.
Dedicated Smartphone & Synchronization
If you need a smartphone as your secured device, consider using one that is not connected to Google or Apple. Open-source Android like CalyxOS or GrapheneOS or Linux-based phones like the Librem 5 or Pinephone offers tech-savvy alternatives.
Once your private phone is up and running, store and sync your contacts using an app and service like Etesync, which is open source and designed around zero-knowledge storage. The tech-savvy will appreciate that Etesync provides the server software to maintain better control of their data.
Nextcloud is another alternative for securing contact (and many other types of) information by controlling storage. The Nextcloud Contacts plugin synchronizes to your smartphone contact app.
Low-Tech Option
The information in your address book changes slowly compared to your calendar or email. This makes it a great candidate to be downgraded to a low-tech option.

Consider keeping your private contacts in a little black address book. But remember that "going analog" comes without backups, sorting, searching, infinitely long listing, and auto-filling contact forms. This is a worthy trade-off for those wanting the highest-level security and privacy.
It's Not You; It's Them
Now that you're handling your contacts more carefully, what do we do about all the businesses, family, and friends with your information?
Companies You Do Business with
When you go to the doctor, the office presents you with a contact form to fill out. As you walk through the blank lines with your pen, be skeptical of whether each line is needed.
Does your doctor truly need your phone number? Well, yes. They have to be able to call you about appointments, results, etc.
Does your doctor truly need your home address? Sure. They have to be able to send me invoices.
Does your doctor truly need your birthdate? Maybe. Some medications have age requirements. Leave it off until asked.
Does your doctor truly need your email address? Maybe. Leave it blank until asked, and then question what it's used for.
Does your doctor truly need your social security or driver's license? Probably not. Leave these off.
Question whenever a business collects your information through an online or in-person contact form. The representative will let you know if they actually need any withheld items. Omit information that is not indeed required.
Don't give up your personal information without questioning why it's needed.
Your Family & Friends
Your first name, last name, email address, and phone number are a goner in the hands of your family and friends. These bits of your information are passed around so often that it'll be nearly impossible to reel them back in completely.
Let's attempt to get some of them to delete your information using the following messages.
From your normal email account, send the following email:
Hey Everyone,
Sorry for the mass email, but I'm shutting down this email address. It's been hacked. I don't want you all to get infected, so I'm being extra cautious.
Remove my email address from your contacts list. Then, text or instant message me for the new one.
-
You can decide whether to change your email address or feign this action.
Phone Number
A similar text might get some to remove your phone number from their address book. Send this text or instant message:
Getting lots of spam callers. At the store getting new number & phone. They transferred your info. I'll send you a text from my new phone. Trading in this one.
(159/160 characters)
Again, you decide whether you actually go through with changing your number. Consider updating each person you sent this message to with "do not answer."
Address
Getting family and friends to drop your physical address is the easiest of the three. Addresses aren't kept as often, with the internet replacing postal mail.
As digital nomads, we move every few years, so everyone knows not to mail us anything. We forwarded all physical mail to Virtual Post Mail and only fill this address in any contact forms.
If you don't move as much, sending this email should work:
Hello Family,
We've had a few important financial statements and kids' birthday cards stolen from our mailbox. We're also tired of getting packages stolen.
We're going to send our mail to a secure mail processor and pick up our packages at the post office, UPS, or FedEx.
Please don't send any physical mail. It'll get stolen. Consider deleting our address as a precaution. Later, if you want to send something to us, I'll give you my work address.
I guess thieves know that anything that's still mailed to a physical address must be valuable.
-
We want to impress upon your family that your address has no value and can be safely deleted. Don't worry. Those that sincerely wish to visit you already know where you live.
Final Thoughts
This highly connected world is a mixed blessing. It's brought about convenience and knowledge-sharing that previous generations could not have imagined. But with a gain in information accessibility, we've lost a share of security and privacy.
Your contacts list is arguably the second-most valuable data behind your password manager vault.
Take a few moments to scroll through your address book, reading the names and various pieces of information you stored. What if that information was posted on the dark web for cheap?
On the flip side, your family and friends likely leak your personal information and perhaps don't even know it. Help educate them by sharing this article.