Cybercrime is on the rise with a global cost of over 10 trillion predicted by 2025. Indeed, there's a growing demand for cyber investigators. But what do these professionals do, and how can you become one?
Cyber investigators analyze digital evidence to uncover hacking, malware development, online fraud, and other cybercrimes. They record investigations in court-useable reports. This job requires digital forensics expertise and the ability to analyze data from numerous sources.
For some, the beloved crime dramas of old - from CSI NY to Cold Case - sparked a fascination with all things related to solving and investigating mysterious crimes. Investigating digital crimes is great for those wishing to go further into this topic in today's digital world. Starting with what a cyber investigator is, here are all the need-to-knows.

What's A Cyber Investigator?
As the world increasingly moves online, so too do the crimes. From identity theft to fraud. A myriad of crimes can be committed through the use of computers and the Internet.
And that's where cyber investigators come in. A cyber investigator is a specialist in gathering, analyzing, and documenting evidence related to computer crimes, also called "cybercrimes."
They use their expertise in forensics and security to investigate incidents such as theft of data, hacking attacks, malware development, and online fraud. They uncover evidence of these crimes and give it to law enforcement so that the perpetrators can be brought to justice.
To do this successfully, they must have an understanding of digital evidence, collection methods as well as analysis techniques and also be familiar with applicable laws.
In addition to their technical expertise, cyber investigators must have strong communication skills as they often have to conduct interviews, prepare reports and testify in court.
After the difficult and painstaking work of a cyber investigation, finding the evidence necessary to testify in court is like seeing a beautiful rainbow after an intense storm.
What Does A Cyber Investigator Do? What Is A Cyber Investigation?
A cyber investigation is an inquiry that focuses on the origins, activities, and implications of any malicious digital activity.
Construction workers and cyber investigators share something in common - the arduous task of assembling seemingly unrelated pieces into a meaningful whole.
To that end, a cyber investigation begins with fragmented, uncertain data that must be organized into information. The information that is relevant and whose credibility is verified forms knowledge for use in legal proceedings. All these components come together as evidence presented in courtrooms around the world.
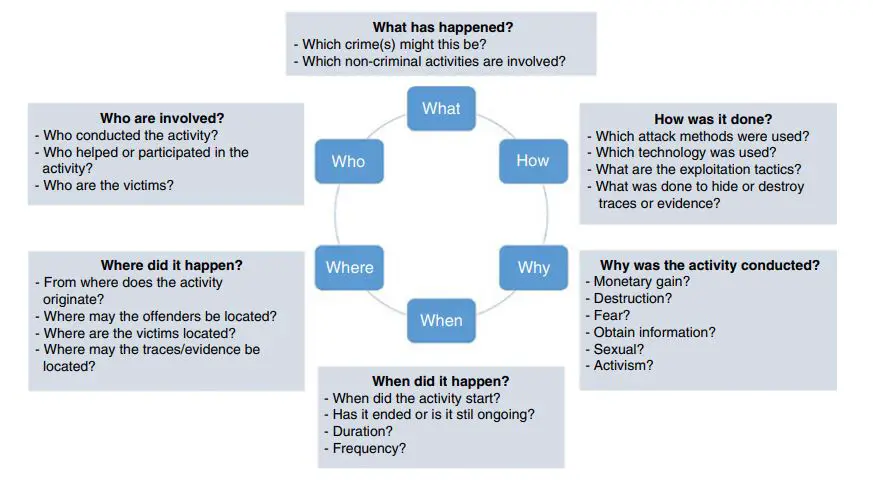
During a cyber investigation, detectives look for clues to uncover the evidence by asking six key questions known as the 5WHs: Who was involved? What happened? Where did it occur? When did it take place? Why did it happen like that ? and how was the event executed? Answering these important queries can help shed light on potentially incriminating activities.
A cyber investigation is often conducted in seven steps. These are:
Step 1: Collect all relevant and available data
A cyber investigator will typically start by identifying the systems and devices that were involved in the incident. They will then collect data from these devices, including user activity logs, system files, and network traffic. This may involve using forensic tools and techniques to reconstruct deleted files.
They may also interview witnesses or suspects, and collect data from social media and other online sources. The goal is to gather as much information as possible and leave no stone unturned.
Step 2: Check That All Data Is Relevant, Reliable, And Accurate
Before presenting any evidence, it is essential to carefully examine a broad volume of data and weed out questionable data.
All inconsistencies must be pinpointed and followed up on to ensure that the facts collected are robust enough to hold water when making accusations or constructing an argument against wrongdoers.
Gathering only valid proof data will help prosecuting agents to effectively build an impenetrable case against cyber criminals.
Step 3: Connect
Through defining data, making connections between them, and structuring it all together, cyber investigators can gain a better insight into how events unfolded and how every element of the case fits in with the rest.
Additionally, creating this structure allows for easy access to important information at any time during an investigation; helping to uncover even more details on what happened.
Step 4: Develop A Plausible Hypothesis
In this step, cyber investigators form all compelling scenarios based on the information gathered. A plausible hypothesis is developed to explain what cybercrime activity may have occurred and how it could have happened.
Step 5: Support Or Refute The Hypothesis
After a hypothesis has been formed, more data is collected to support or disprove it. This step examines if the theory stands up to scrutiny or if any holes in it need to be filled.
Step 6: Consult
To ensure a comprehensive and impartial inquiry, it is essential to bring in an outside perspective during any cyber investigation - like recruiting someone outside the existing investigative team. Doing so guards against potential blind spots or tunnel vision that could otherwise go unnoticed.
Step 7: Present
The last step is to explain the findings of the investigation in a way that can be understood, either through reports or in court.
These steps require a variety of skills from cyber investigators. This includes the use of forensic tools and techniques, communication and interview skills, and legal expertise. These are the skills that are usually required for most cyber investigator jobs.

Job Description Of A Cyber Investigator
With cybercrime on the upswing, it is easy to see why a career in investigating cyberspace could be so attractive. Each year, nearly 700 million people fall victim and businesses take almost 200 days until they can detect a cyber attack.
For those looking for adventure, excitement and the opportunity of helping others outwit malicious online activity - being a Cyber Investigator may just fit the bill. So what does this job entail? Here's your sneak-peak job description of one of today’s most sought-after career:
Conduct digital forensic investigations to uncover malicious activity such as identity theft, data breaches, and other computer-related crimes and establish the facts of what happened
Analyze complex data sets from various sources to gather evidence, including network traffic logs, system files, and user activity logs
Work with IT staff, law enforcement agencies, attorneys, and other stakeholders to ensure the investigation is conducted properly
Conduct interviews with witnesses and suspects
Prepare detailed reports of investigations and present findings in court or during legal proceedings
Stay up-to-date with digital forensics trends, tools, and technologies
Cyber Investigator And Similar Job Titles
Some job posts may use a different job title to describe a cyber investigator. Here are some of the other job titles that can be used that may require similar skills: Cybercrime Investigator, Cyber Fraud Investigator, Internet Crime Investigator, Cyber Crime Analyst, and Computer Forensics Investigator.
How Do You Become a Cyber Investigator?
There is no one-size-fits-all answer to this question. However,
a Bachelor's degree in Criminal Justice, or Cybersecurity, or Computer Forensics can open doors for a successful career as a cyber investigator, as could popular certifications such as CompTIA Security+, CompTIA CASP, and Certified Information Privacy Professional (CISP).
3 Tips Necessary To Become A Successful Cyber Investigator
To get ahead in cyber investigations, here are three indispensable tips:
First, when carrying out an investigation, do your level best to apply the ABC rule. Assume Nothing, Believe Nothing, and Challenge/ Check Everything. This will help you to stay impartial and ethical as you assess evidence and testimonies.
Secondly, when handling digital evidence, strive to preserve evidence integrity by following the chain of custody protocols. This helps to ensure that all evidence processed is genuine, and admissible in court.
Finally, you must stay up-to-date with current trends and practices within the realm of digital forensics. As technology advances, so does cybercrime; staying abreast can help you successfully investigate any case
In conclusion, cyber investigations are a crucial part of keeping the world safe from digital attacks and crimes. If you want to become a successful cyber investigator, like with any other computer career, you need to have the right skills, knowledge, and certifications to get the job done.